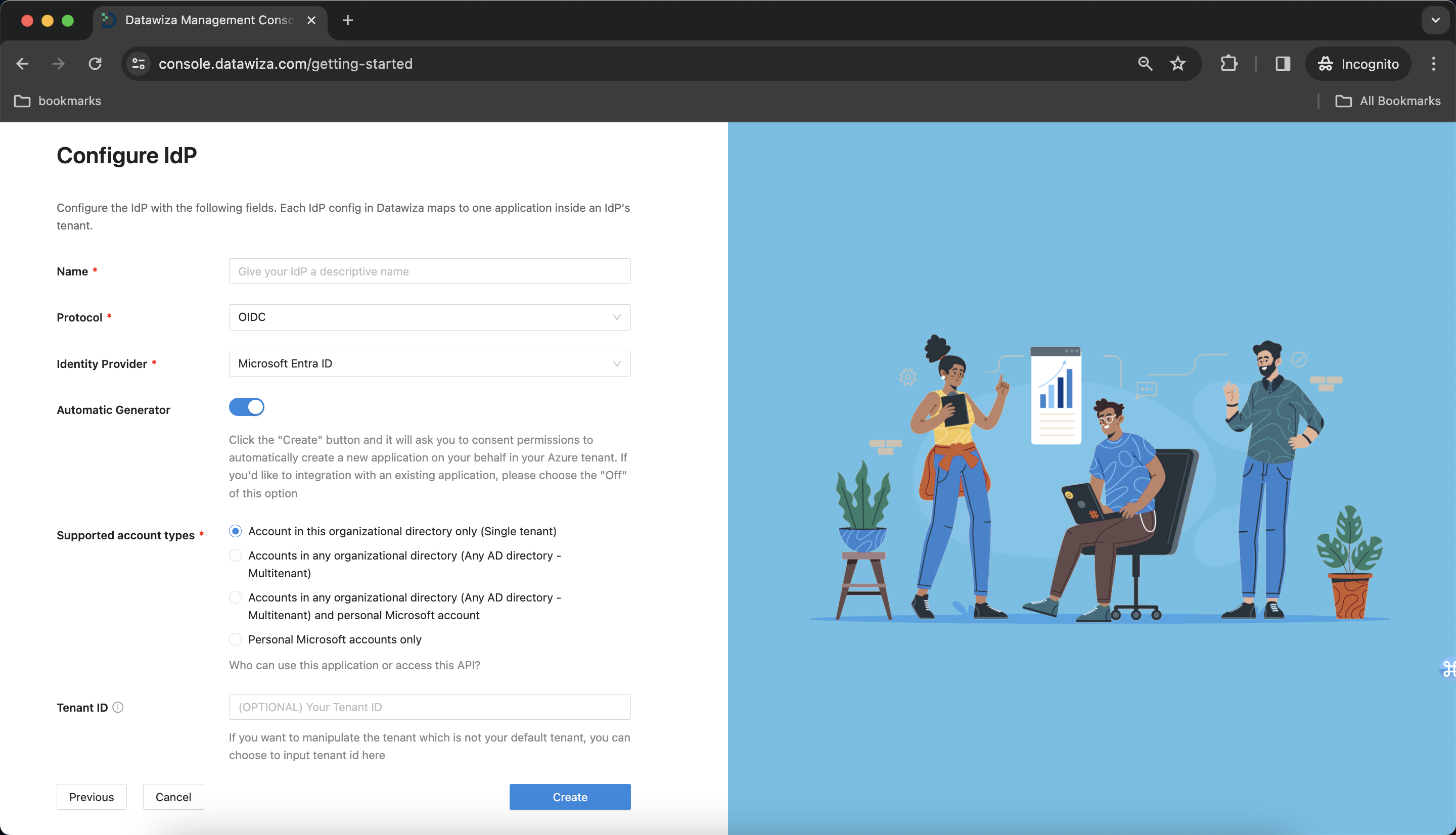
Secure Multiple Web Apps Using Different IdPs
Enable SSO for Multiple Applications with Different Identity Providers
Preview
In this tutorial, we will use the Datawiza Access Proxy (DAP) to enable SSO for two Flask applications serving static HTML. For our scenario, one web app will be the homepage for the managers of our company, while the other web app will be the homepage for the engineers. The goal of this tutorial is to see how we can add multiple applications to a single deployment within the Datawiza Cloud Management Console (DCMC), and how we can associate different Identity Providers to each of our applications.
- Both of our applications will be running on our local docker network,
172.17.0.1. The manager homepage will run on172.17.0.1:3001and the engineer homepage will be on172.17.0.1:3002. - The DAP will run on
localhostin a container and expose two ports:9772and9773. Traffic to either of our applications will reach DAP first and then be proxied to our applications. Traffic tolocalhost:9772will be proxied to172.17.0.1:3001and traffic tolocalhost:9773will be proxied to172.17.0.1:3002.
Part I: Identity Provider Configuration
You will need to register each application with an Identity Provider. For this exercise, we will register the app for the managers with Microsoft Entra ID (Azure AD) and the app for the engineers with Okta. Please follow IdP Configuration Guide: Microsoft Entra ID and IdP Configuration Guide: Okta for specific configuration instructions.
Part II: Create Deployment and Applications on Datawiza Cloud Management Console (DCMC)
After configuring your desired Identity Provider, we need to create a new deployment on the DCMC which will contain our two applications. We will also generate a keypair (PROVISIONING_KEY, PROVISIONING_SECRET) in order for the DAP to get the latest configurations and policies from the DCMC.
Sign Into DCMC
- Login to the DCMC.
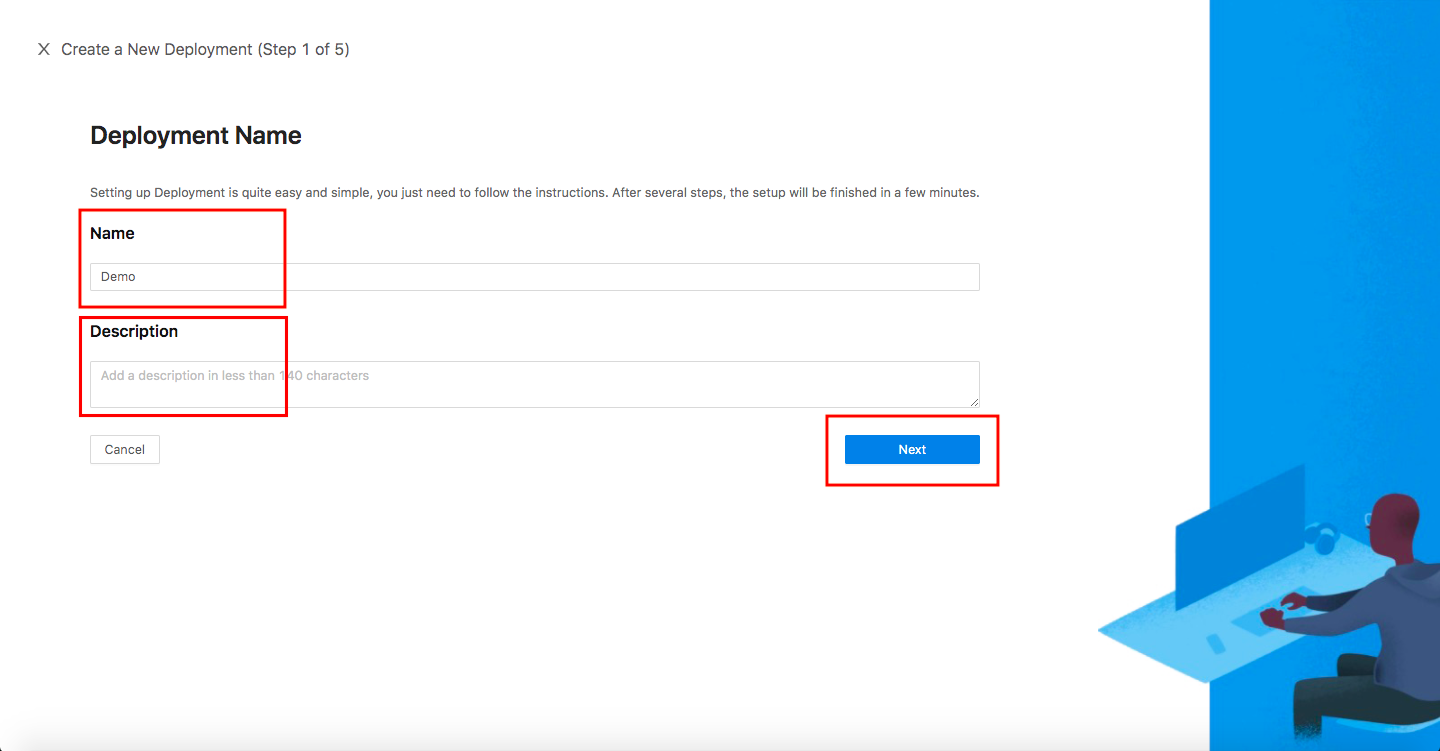
Create New Deployment
- Click the orange button
Getting startedand specify aNameand aDescription. ClickSave.
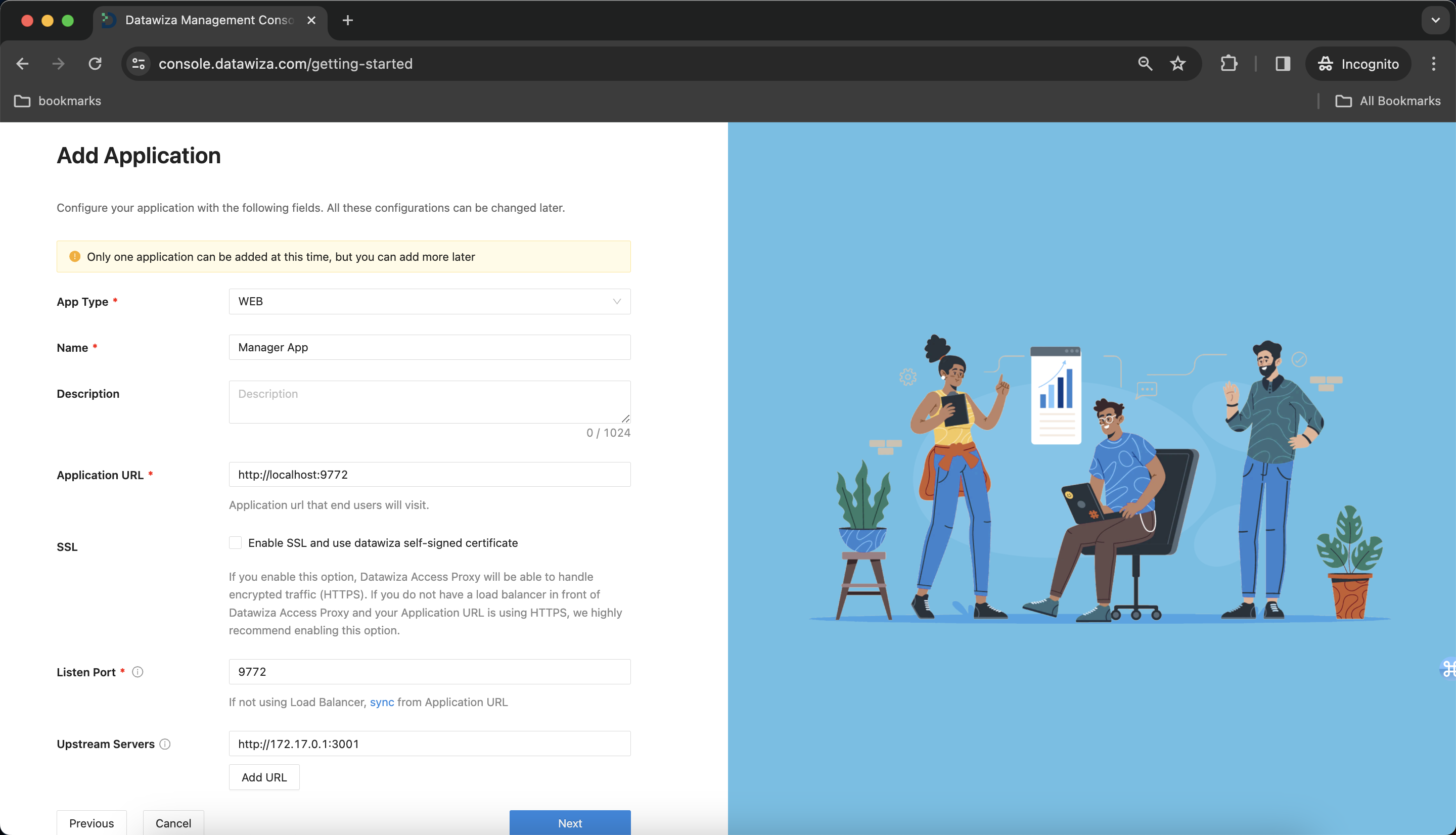
Add Manager Application
Configure our application for the managers with the following fields:
App Type:WebName: Manager AppApplication URL:http://localhost:9772Listen Port:9772Upstream Servers:http://172.17.0.1:3001- Select
Next.
IdP Configuration
- Choose
Microsoft Entra IDfrom the drop down menu. We'll addMicrosoft Entra IDfirst, and then addOktaas an additional IdP later.
Populate the fields of the form with the keys/values obtained from IdP Configuration Guide: Microsoft Entra ID.
Alternatively, you can use One Click Integration to configure the Microsoft Entra ID.
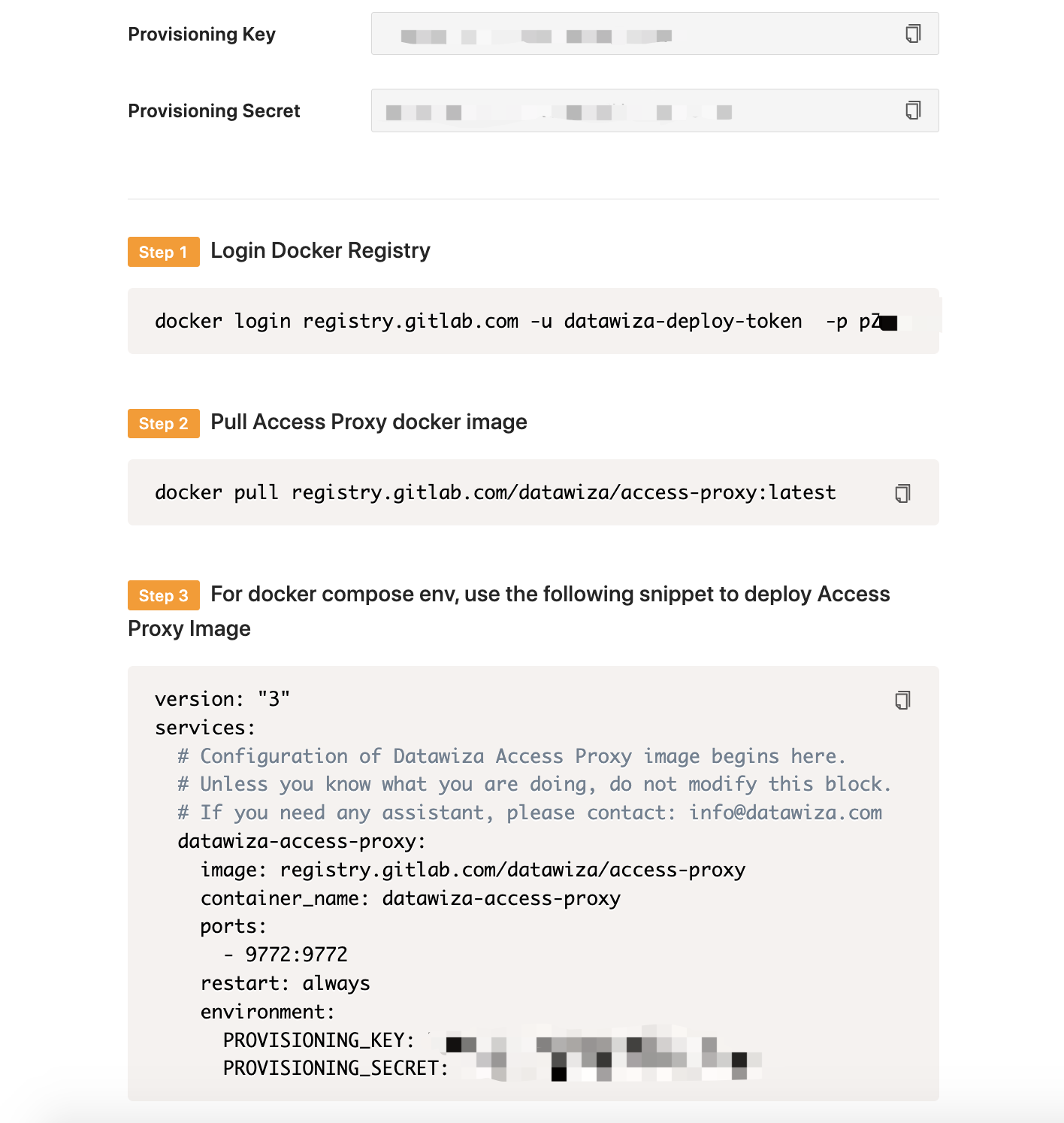
Note Down Provisioning Keys
Note down your PROVISIONING_KEY and PROVISIONING_SECRET. We will need these values later when deploying the DAP.
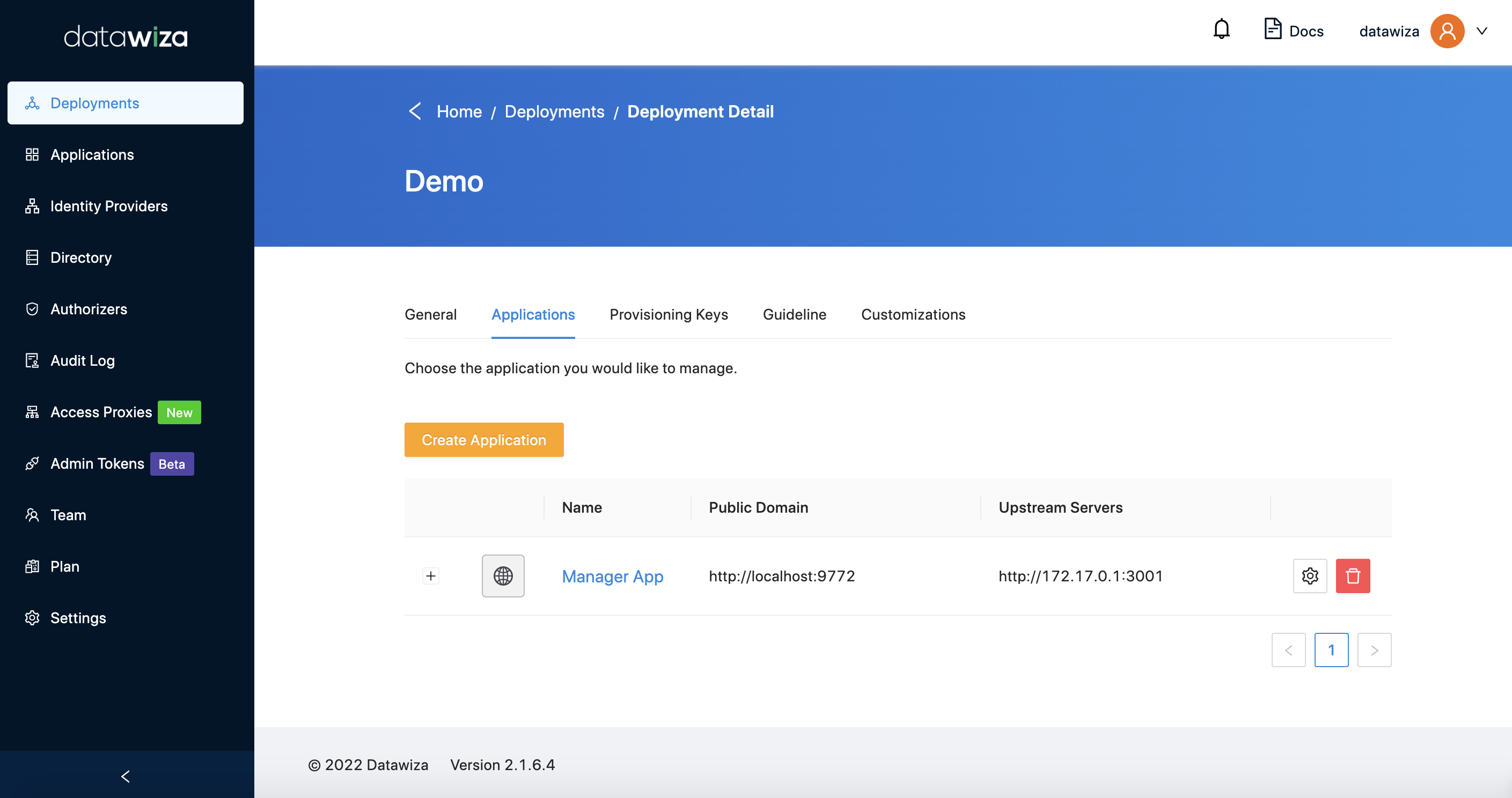
Add Engineer Application
- Select the
Applicationstab. Select the orange buttonCreate Application. You should already seeManager Appin the deployment.
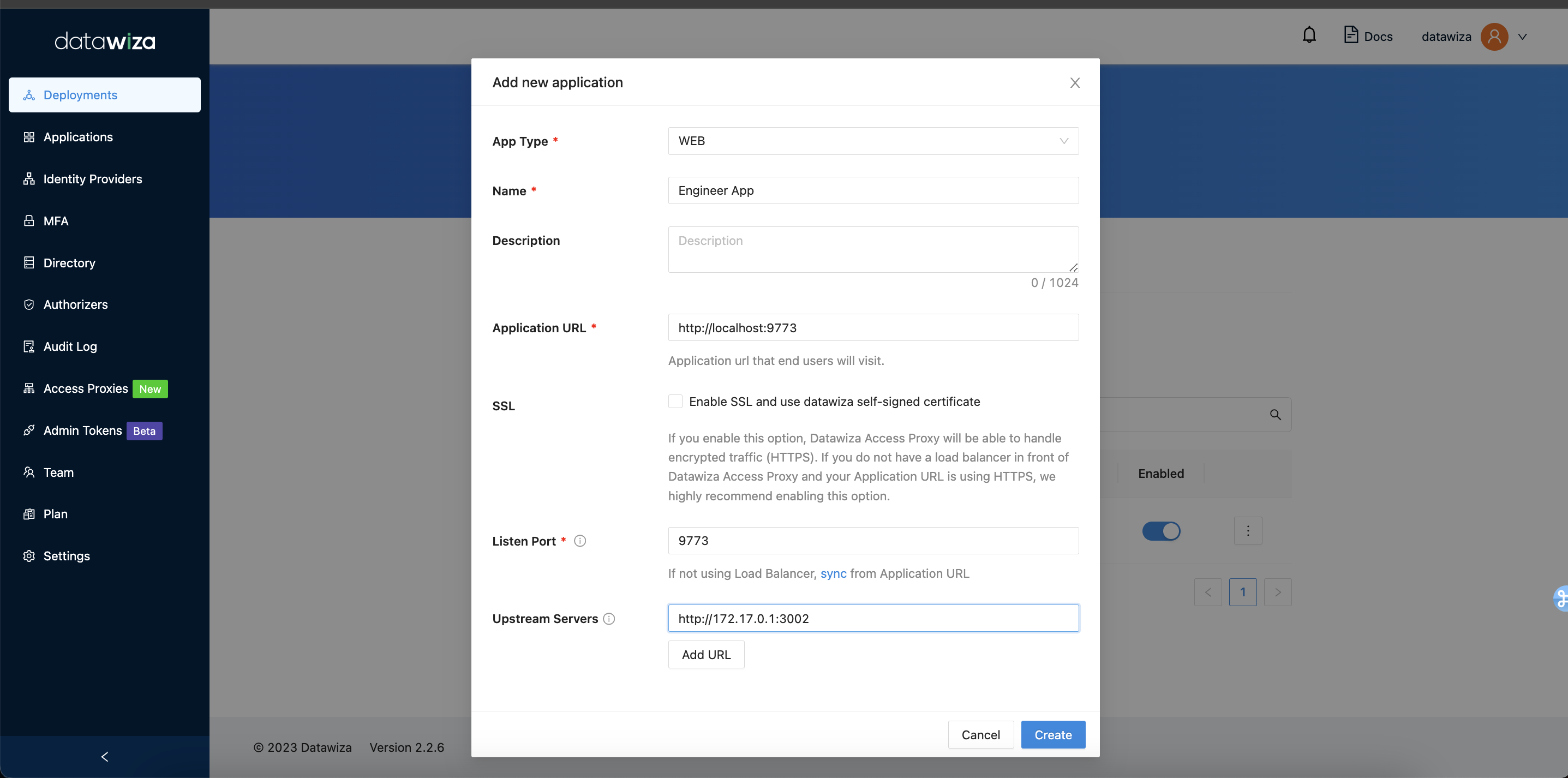
- Configure our application for the engineers with the following fields:
App Type:WebName:Engineer AppApplication URL:http://localhost:9773Listen Port:9773Upstream Servers:http://172.17.0.1:3002- Select
Create.
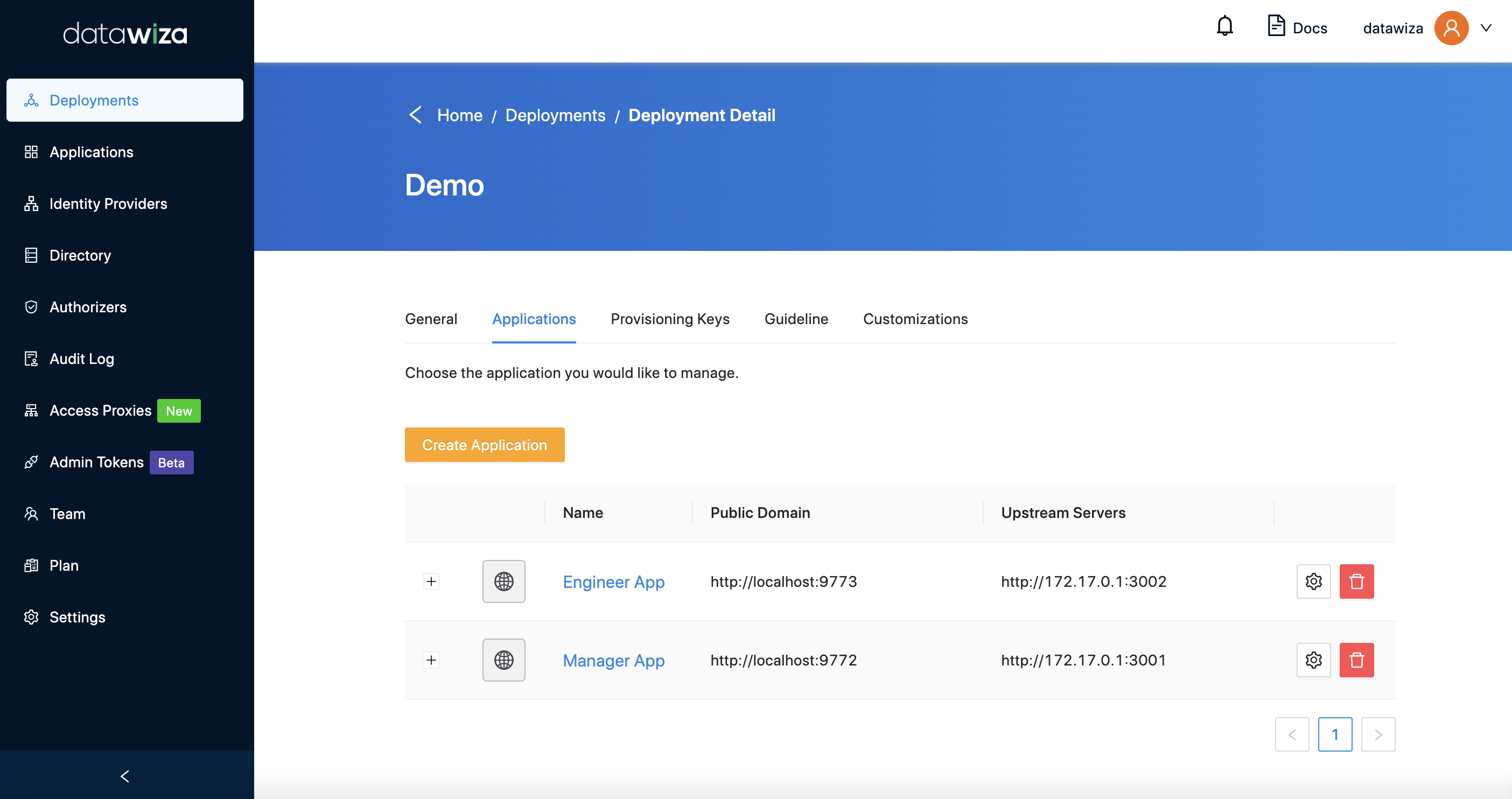
You should now see both the Manager App and the Engineer App within the deployment.
Assigning IdPs to our Applications
- Return to the
Applicationstab. Select theEngineer App, and go toIdP Configuration. SelectAssign IdP. From the drop down menu, you should see the IdPs that we have added to the DCMC. AssignMicrosoft Entra IDto theManager AppandOktato theEngineer App.
Part III: Run DAP With Our Applications
We can use either docker or docker-compose to run the DAP. The following is an example of a docker-compose.yml file. You may need to login to our container registry to download the images of the Access Proxy. See Step3: Congifure DAP and SSO Integration for more details.
version: '3'
services:
datawiza-access-proxy:
# Using the latest image
image: registry.gitlab.com/datawiza/access-proxy:latest
container_name: datawiza-access-proxy
restart: always
ports:
- "9772:9772"
- "9773:9773"
environment:
PROVISIONING_KEY: #########################
PROVISIONING_SECRET: #########################
After executing docker-compose -f docker-compose.yml up, Manager App should have SSO enabled with Microsoft Entra ID. Open a browser and visit http://localhost:9772/. You should see the Microsoft Entra ID login page as follows:
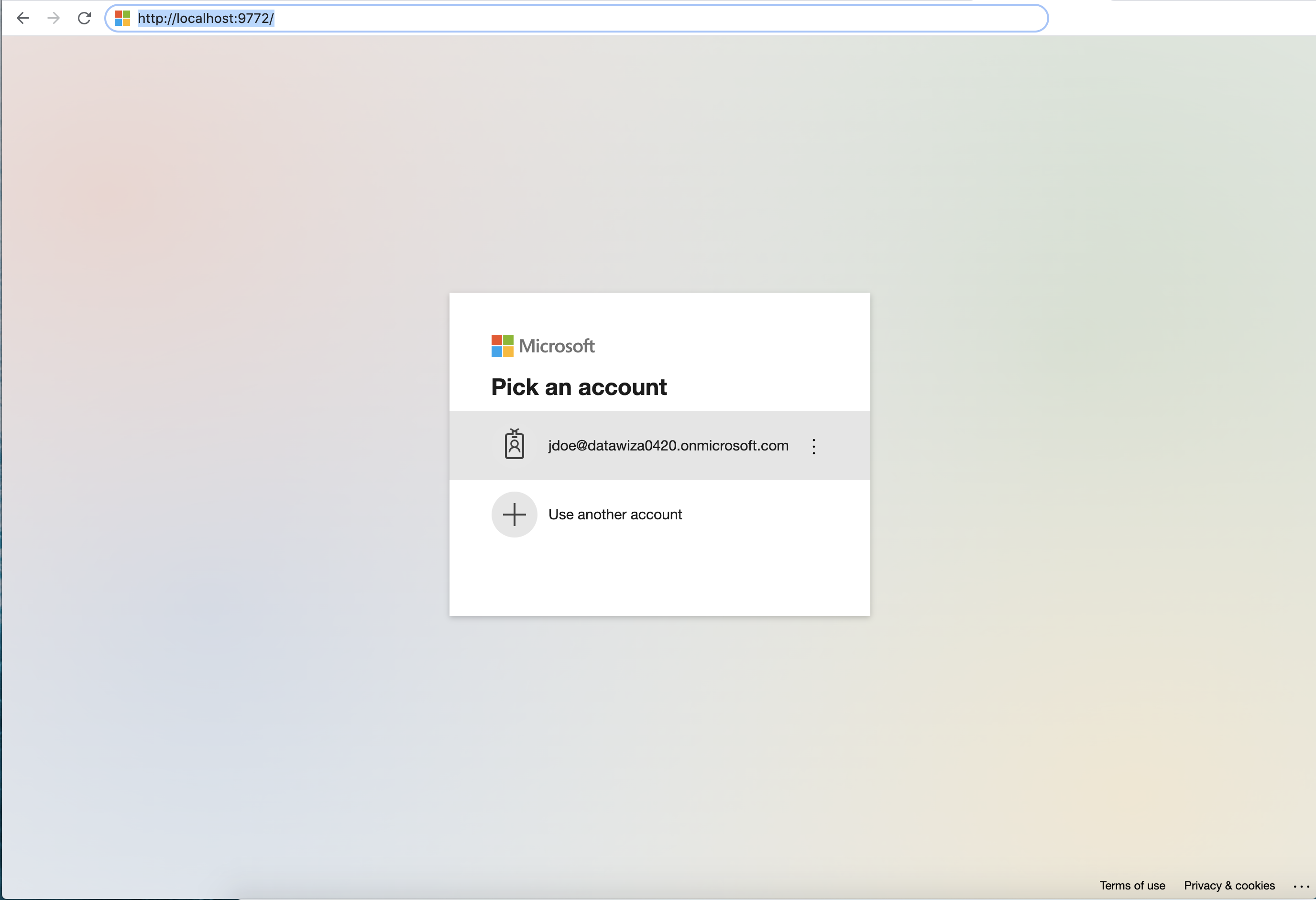
If you are seeing the Microsoft Entra ID login page but are unable to login (Microsoft keeps asking for your username and password repeatedly), ensure that you have created a user for your AD domain. Logging in with the root account will not work. Your username should be in the form of user@your_domain.onmicrosoft.com. Note that if you are already logged into Microsoft Entra ID in your browser, you may need to logout to see the login page.
After successfully logging in, we can see our manager homepage:

To test out the engineer homepage, we visit http://localhost:9773. We are greeted with the following Okta login page:
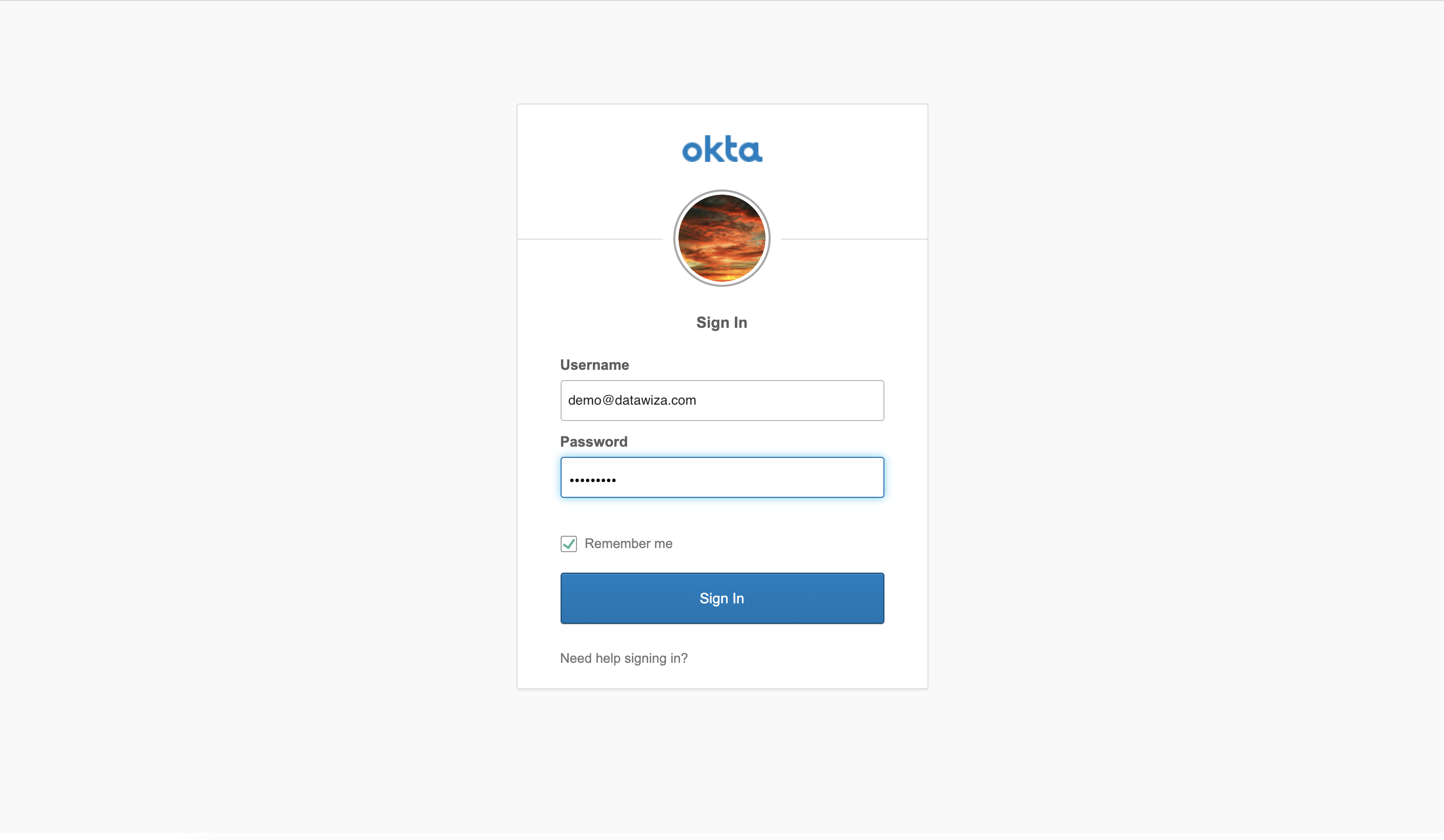
After successfully logging in, we can see our engineer homepage:
Summary
In summary, we have seen how to deploy the DAP and implement SSO alongside multiple applications, each using different identity providers. Please refer to Step4: Pass User Attributes and Step5: Achieve Granular Access Control to interact with the other features provided by the Datawiza Access Proxy.