Integrate Datawiza Access Proxy with Microsoft Sentinel
Overview
In this tutorial, we will guide you how to send Datawiza Access Proxy logs to Microsoft Sentinel for advanced security monitoring and threat detection.
After the configuration is finished, you'll inspect the results in Log Analytics.
The steps required to configure as follows:
- Create a Microsoft Entra application to authenticate against the API.
- Create a data collection endpoint (DCE) to receive data.
- Create a custom table in a Log Analytics workspace. This is the table you'll be sending data to. As part of this process, you will create a data collection rule (DCR) to direct the data to the target table.
- Give the Entra ID application access to the DCR.
- Install Datawiza Sentinel Connector.
Benefits of Integrating
Integrating DAP logs with Microsoft Sentinel allows organizations to:
- Enable real-time monitoring of access logs.
- Detect security threats using Microsoft Sentinel.
- Centralize log storage and analysis for better insights.
Prerequisites
To complete this tutorial, you need:
- A Log Analytics workspace where you have at least contributor rights.
- Permissions to create DCR objects in the workspace.
Configuration Steps
Create a Microsoft Entra Application
Start by registering a Microsoft Entra application to authenticate against the API. Any Resource Manager authentication scheme is supported, but this tutorial will follow the Client Credential Grant Flow scheme.
- On the Microsoft Entra ID menu in the Azure portal, select App registrations > New registration.
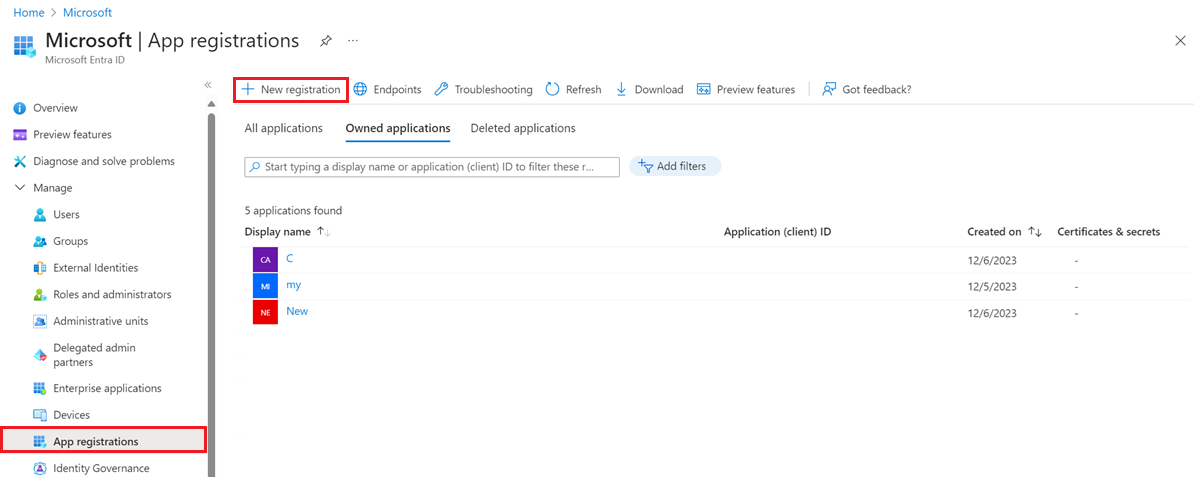
- Give the application a name and change the tenancy scope if the default isn't appropriate for your environment. A Redirect URI isn't required.
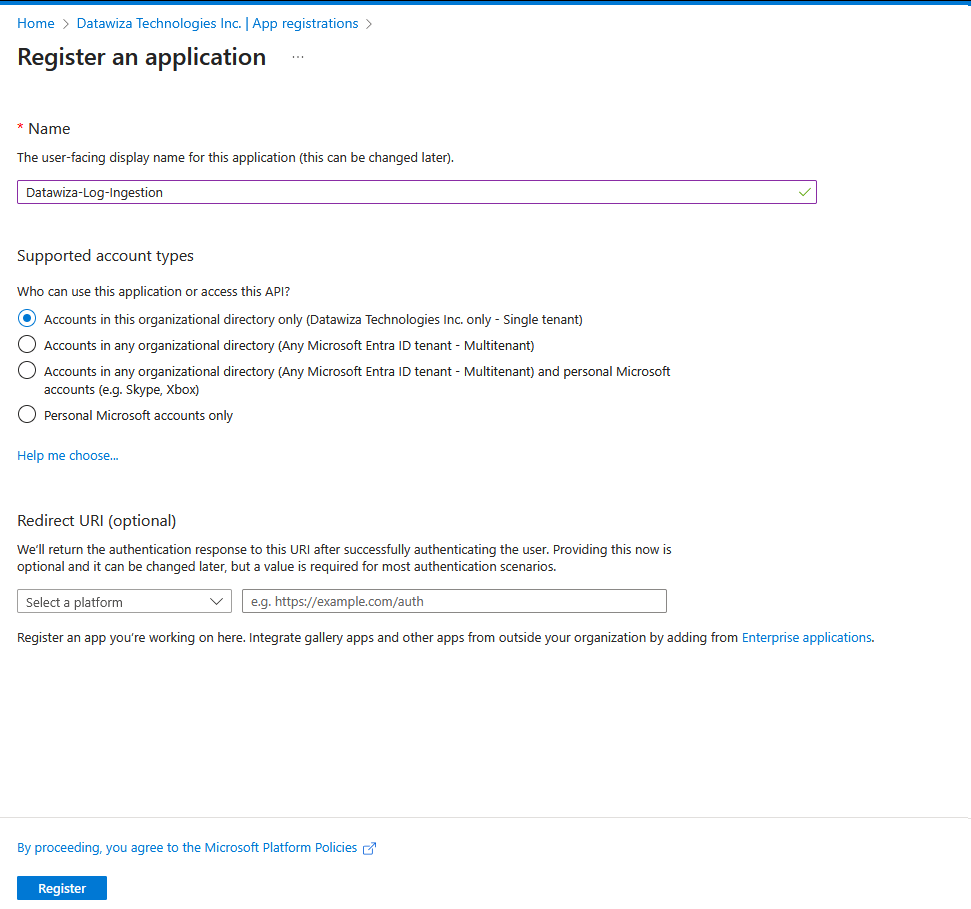
- After registration, you can view the details of the application. Note the Application (client) ID and the Directory (tenant) ID. You'll need these values later in the process.
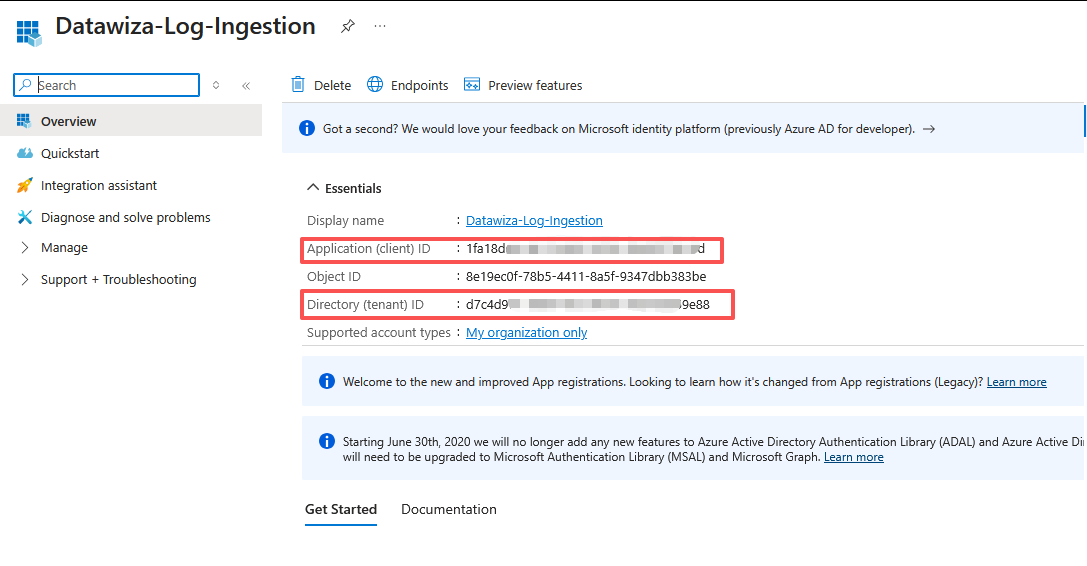
- You now need to generate an application client secret, which is similar to creating a password to use with a username. Select Certificates & secrets > New client secret. Give the secret a name to identify its purpose and select an Expires duration. The value 1 year is selected here. For a production implementation, you would follow best practices for a secret rotation procedure or use a more secure authentication mode, such as a certificate.
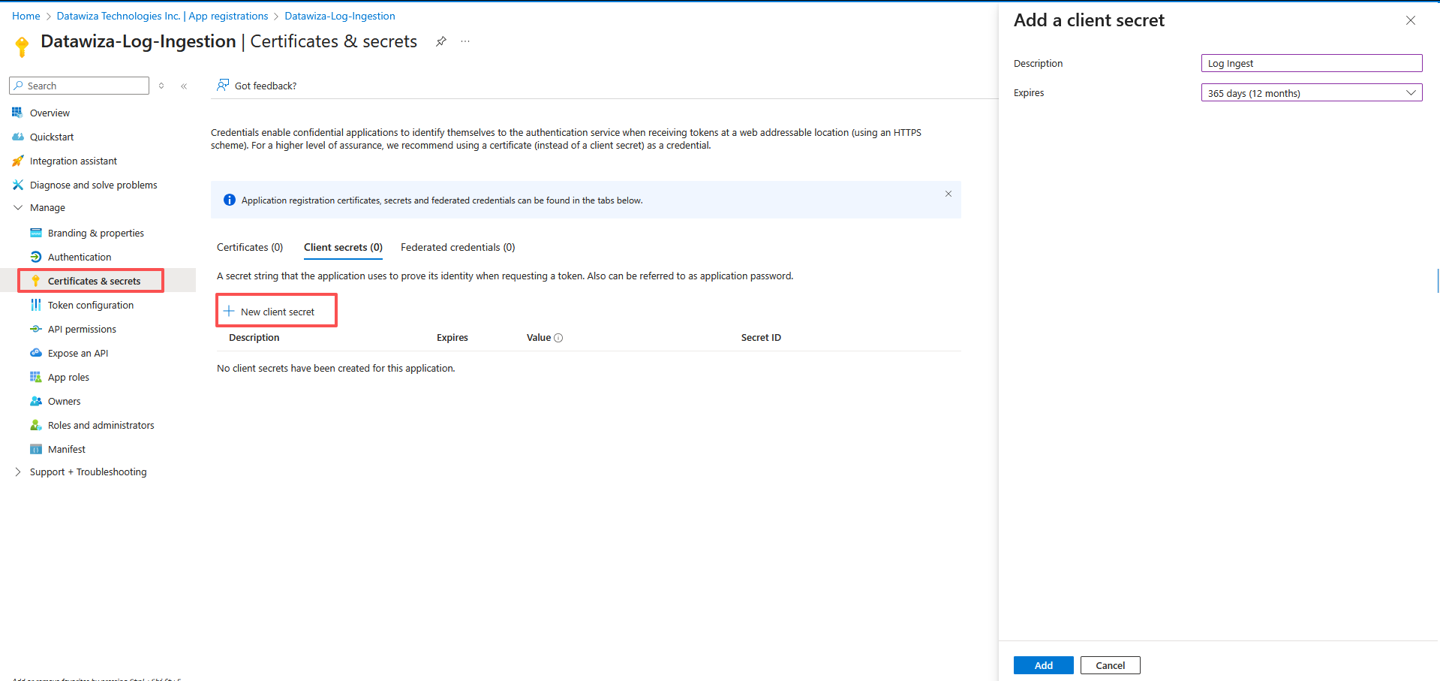
- Select Add to save the secret and then note the Value. Ensure that you record this value because you can't recover it after you move away from this page. Use the same security measures as you would for safekeeping a password because it's the functional equivalent.

Create data collection endpoint
A data collection endpoint is required to accept the data. The DCE needs to be in the same region as the Log Analytics workspace where the data will be sent or the data collection rule being used.
- To create a new DCE, go to the Monitor menu in the Azure portal. Select Data Collection Endpoints and then select Create.
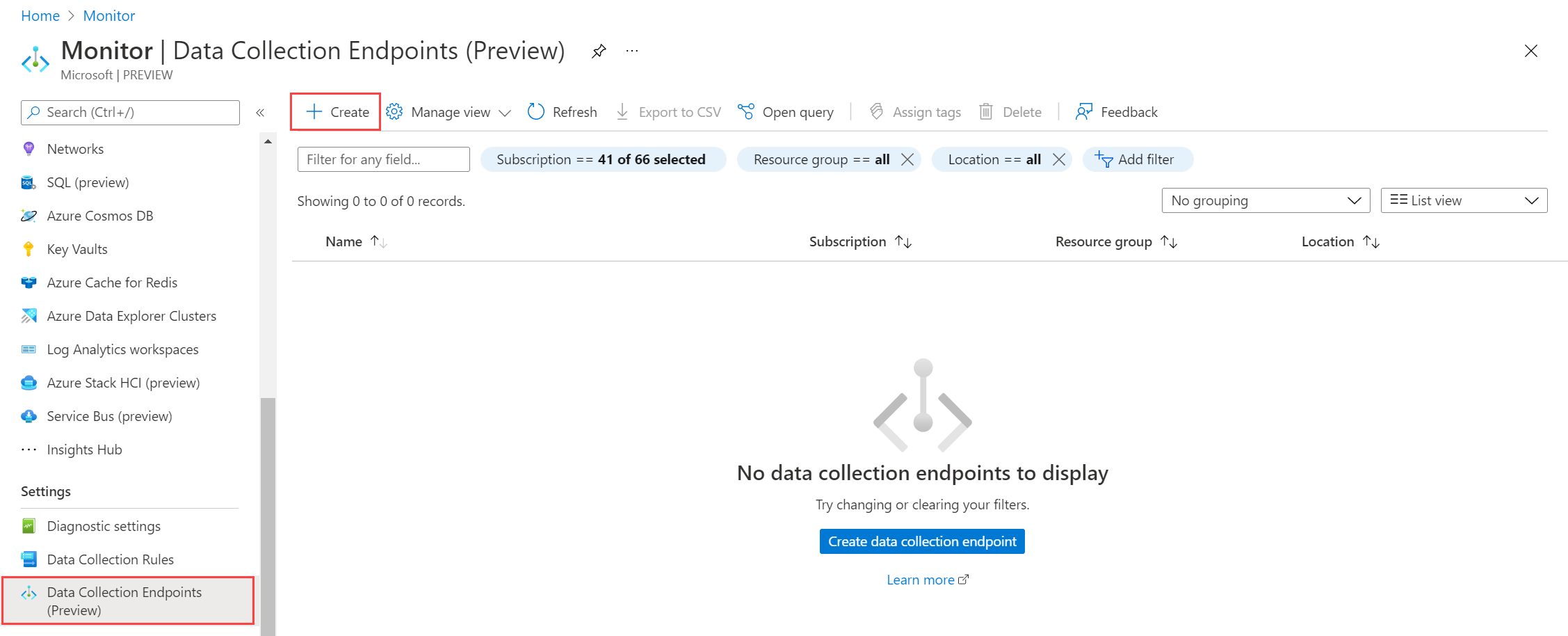
- Provide a name for the DCE and ensure that it's in the same region as your workspace. Select Create to create the DCE.
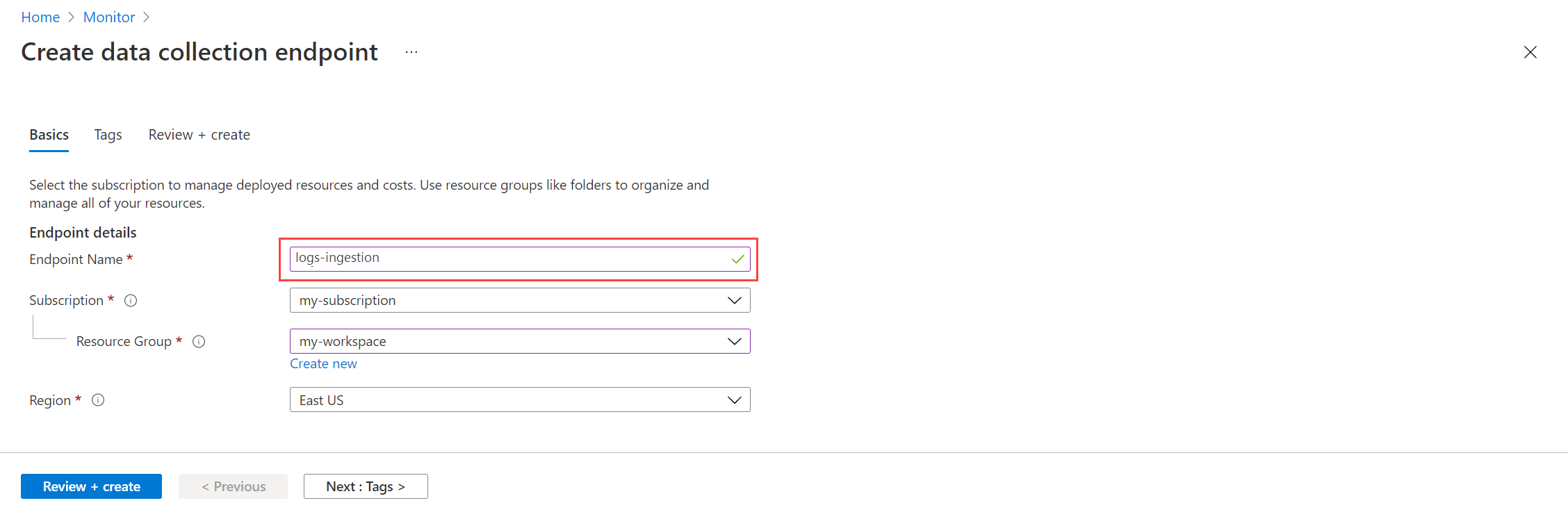
- After the DCE is created, select it so that you can view its properties. Note the Logs ingestion URI because you'll need it in a later step.

Create new table in Log Analytics workspace
Before you can send data to the workspace, you need to create the custom table where the data will be sent.
- Go to the Log Analytics workspaces menu in the Azure portal and select Tables. The tables in the workspace will appear. Select Create > New custom log (Direct Ingest).
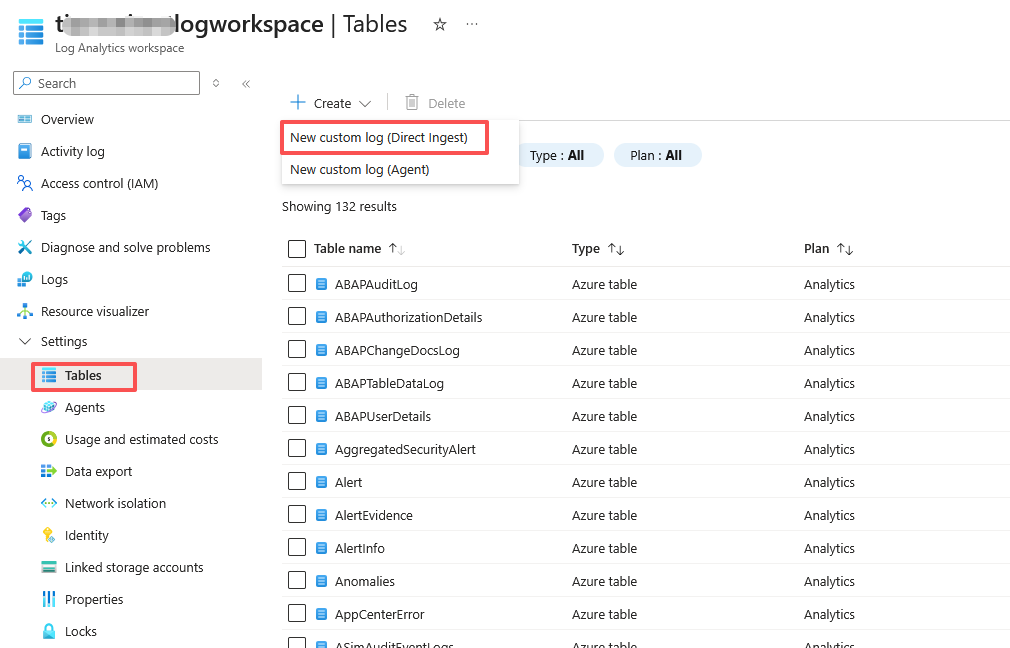
- Specify a name for the table. You don't need to add the _CL suffix required for a custom table because it will be automatically added to the name you specify.
- Select Create a new data collection rule to create the DCR that will be used to send data to this table. If you have an existing DCR, you can choose to use it instead. Specify the Subscription, Resource group, and Name for the DCR that will contain the custom log configuration.
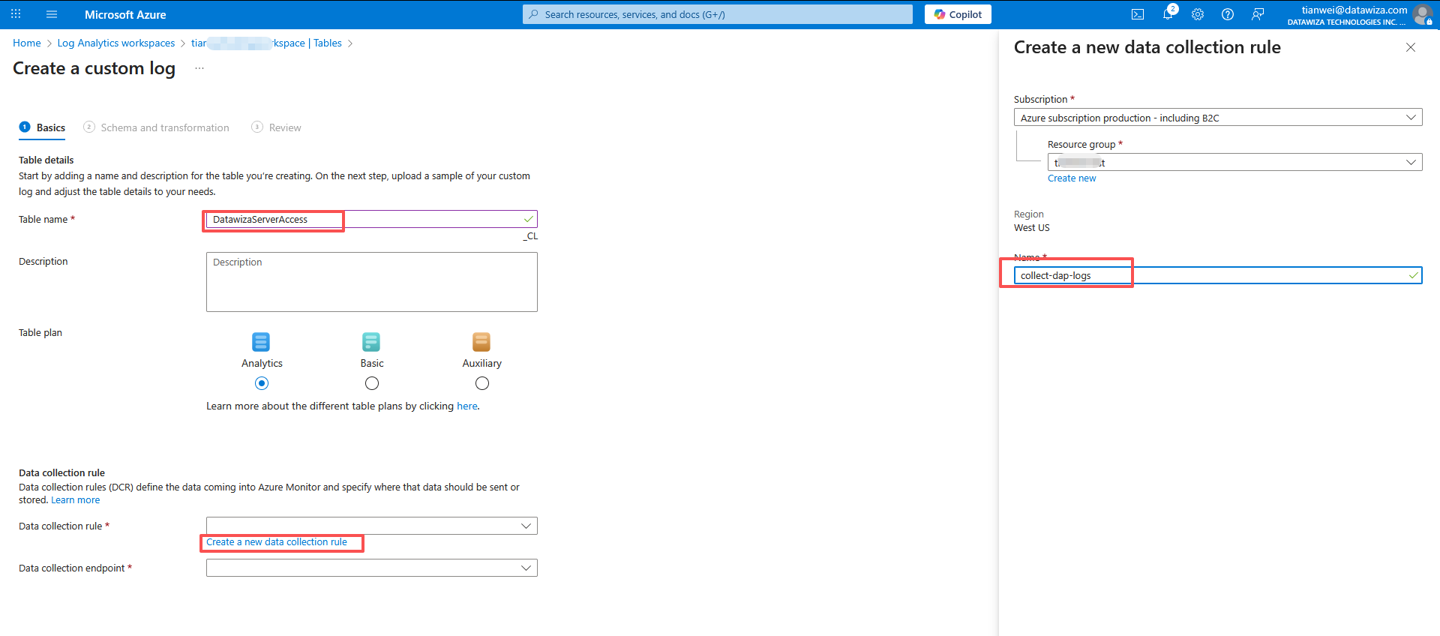
- Select a DCE that you already created from the pull-down menu and select Next.

Parse and filter sample data
Instead of directly configuring the schema of the table, you can upload a file with a sample JSON array of data through the portal, and Azure Monitor will set the schema automatically.
Copy the sample data and save it as
data_sample.json.[ { "host": { "name": "08a90228a3f1" }, "message": "{\"customer_id\":\"ef59b320-f822-4fa6-8699-75b5b9ac7a1d\",\"version\":\"1.9.15\",\"request_id\":\"3aa99f68f6d7777bd22cccb33d69ce52\",\"hostvalue\":\"header.datawiza.net\",\"@timestamp\":\"2025-09-30T13:06:42.504+00:00\",\"timestamp_in_ms\":\"1759237602.504\",\"client_ip\":\"172.27.0.1\",\"hostname\":\"012504f29ca2\",\"content_type\":\"\",\"sent_http_content_type\":\"text/plain\",\"sent_http_content_encoding\":\"gzip\",\"referer\":\"https://header.datawiza.net/\",\"user_agent\":\"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0\",\"x_forwarded_for\":\"\",\"remote_addr\":\"172.27.0.1\",\"method\":\"GET\",\"request_time_in_sec\":0.000,\"upstream_response_time_in_sec\":\"\",\"upstream_header_time_in_sec\":\"\",\"upstream_connect_time_in_sec\":\"\",\"ap_run_time_in_ms\":0,\"server_name\":\"header.datawiza.net\",\"server_port\":443,\"server_protocol\":\"HTTP/1.1\",\"http_status\":200,\"uri\":\"/ab-userinfo\",\"http_host\":\"header.datawiza.net\",\"server_addr\":\"172.27.0.2\",\"urlstr\":\"https://header.datawiza.net/datawiza/ab-userinfo\",\"upstream_addr\":\"\",\"request_length\":651,\"bytes_sent\":2011,\"pid\":\"432\",\"sent_http_location\":\"\",\"user_name\":\"\",\"app_user_name\":\"\",\"opa_status\":\"\",\"rule_action\":\"\",\"rule_id\":\"\"}\r", "log": { "file": { "path": "/var/log/data/server-json.log" } }, "event": { "original": "{\"customer_id\":\"ef59b320-f822-4fa6-8699-75b5b9ac7a1d\",\"version\":\"1.9.15\",\"request_id\":\"3aa99f68f6d7777bd22cccb33d69ce52\",\"hostvalue\":\"header.datawiza.net\",\"@timestamp\":\"2025-09-30T13:06:42.504+00:00\",\"timestamp_in_ms\":\"1759237602.504\",\"client_ip\":\"172.27.0.1\",\"hostname\":\"012504f29ca2\",\"content_type\":\"\",\"sent_http_content_type\":\"text/plain\",\"sent_http_content_encoding\":\"gzip\",\"referer\":\"https://header.datawiza.net/\",\"user_agent\":\"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0\",\"x_forwarded_for\":\"\",\"remote_addr\":\"172.27.0.1\",\"method\":\"GET\",\"request_time_in_sec\":0.000,\"upstream_response_time_in_sec\":\"\",\"upstream_header_time_in_sec\":\"\",\"upstream_connect_time_in_sec\":\"\",\"ap_run_time_in_ms\":0,\"server_name\":\"header.datawiza.net\",\"server_port\":443,\"server_protocol\":\"HTTP/1.1\",\"http_status\":200,\"uri\":\"/ab-userinfo\",\"http_host\":\"header.datawiza.net\",\"server_addr\":\"172.27.0.2\",\"urlstr\":\"https://header.datawiza.net/datawiza/ab-userinfo\",\"upstream_addr\":\"\",\"request_length\":651,\"bytes_sent\":2011,\"pid\":\"432\",\"sent_http_location\":\"\",\"user_name\":\"\",\"app_user_name\":\"\",\"opa_status\":\"\",\"rule_action\":\"\",\"rule_id\":\"\"}\r" }, "ls_timestamp": "2025-10-22T07:05:54.205940699Z", "ls_version": "1" }, { "host": { "name": "08a90228a3f1" }, "message": "{\"customer_id\":\"ef59b320-f822-4fa6-8699-75b5b9ac7a1d\",\"version\":\"1.9.15\",\"request_id\":\"d96ed82ae6e73f081d5cbe317b04db7f\",\"hostvalue\":\"header.datawiza.net\",\"@timestamp\":\"2025-10-07T04:43:04.679+00:00\",\"timestamp_in_ms\":\"1759812184.687\",\"client_ip\":\"172.27.0.1\",\"hostname\":\"012504f29ca2\",\"content_type\":\"\",\"sent_http_content_type\":\"font/woff2\",\"sent_http_content_encoding\":\"\",\"referer\":\"https://header.datawiza.net/vendor/fonts/css/all.min.css\",\"user_agent\":\"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0\",\"x_forwarded_for\":\"\",\"remote_addr\":\"172.27.0.1\",\"method\":\"GET\",\"request_time_in_sec\":0.008,\"upstream_response_time_in_sec\":\"0.008\",\"upstream_header_time_in_sec\":\"0.008\",\"upstream_connect_time_in_sec\":\"0.000\",\"ap_run_time_in_ms\":0,\"server_name\":\"header.datawiza.net\",\"server_port\":443,\"server_protocol\":\"HTTP/1.1\",\"http_status\":200,\"uri\":\"/vendor/fonts/webfonts/fa-brands-400.woff2\",\"http_host\":\"header.datawiza.net\",\"server_addr\":\"172.27.0.2\",\"urlstr\":\"https://header.datawiza.net/vendor/fonts/webfonts/fa-brands-400.woff2\",\"upstream_addr\":\"127.0.0.1:9902\",\"request_length\":767,\"bytes_sent\":78688,\"pid\":\"489\",\"sent_http_location\":\"\",\"user_name\":\"\",\"app_user_name\":\"\",\"opa_status\":\"200\",\"rule_action\":\"passthrough\",\"rule_id\":\"92342ed67e8e41f2afa27a250cd913ef\"}\r", "log": { "file": { "path": "/var/log/data/server-json.log" } }, "event": { "original": "{\"customer_id\":\"ef59b320-f822-4fa6-8699-75b5b9ac7a1d\",\"version\":\"1.9.15\",\"request_id\":\"d96ed82ae6e73f081d5cbe317b04db7f\",\"hostvalue\":\"header.datawiza.net\",\"@timestamp\":\"2025-10-07T04:43:04.679+00:00\",\"timestamp_in_ms\":\"1759812184.687\",\"client_ip\":\"172.27.0.1\",\"hostname\":\"012504f29ca2\",\"content_type\":\"\",\"sent_http_content_type\":\"font/woff2\",\"sent_http_content_encoding\":\"\",\"referer\":\"https://header.datawiza.net/vendor/fonts/css/all.min.css\",\"user_agent\":\"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0\",\"x_forwarded_for\":\"\",\"remote_addr\":\"172.27.0.1\",\"method\":\"GET\",\"request_time_in_sec\":0.008,\"upstream_response_time_in_sec\":\"0.008\",\"upstream_header_time_in_sec\":\"0.008\",\"upstream_connect_time_in_sec\":\"0.000\",\"ap_run_time_in_ms\":0,\"server_name\":\"header.datawiza.net\",\"server_port\":443,\"server_protocol\":\"HTTP/1.1\",\"http_status\":200,\"uri\":\"/vendor/fonts/webfonts/fa-brands-400.woff2\",\"http_host\":\"header.datawiza.net\",\"server_addr\":\"172.27.0.2\",\"urlstr\":\"https://header.datawiza.net/vendor/fonts/webfonts/fa-brands-400.woff2\",\"upstream_addr\":\"127.0.0.1:9902\",\"request_length\":767,\"bytes_sent\":78688,\"pid\":\"489\",\"sent_http_location\":\"\",\"user_name\":\"\",\"app_user_name\":\"\",\"opa_status\":\"200\",\"rule_action\":\"passthrough\",\"rule_id\":\"92342ed67e8e41f2afa27a250cd913ef\"}\r" }, "ls_timestamp": "2025-10-22T07:05:54.214994946Z", "ls_version": "1" } ]Select Browse for files and locate the
data_sample.jsonfile that you previously created.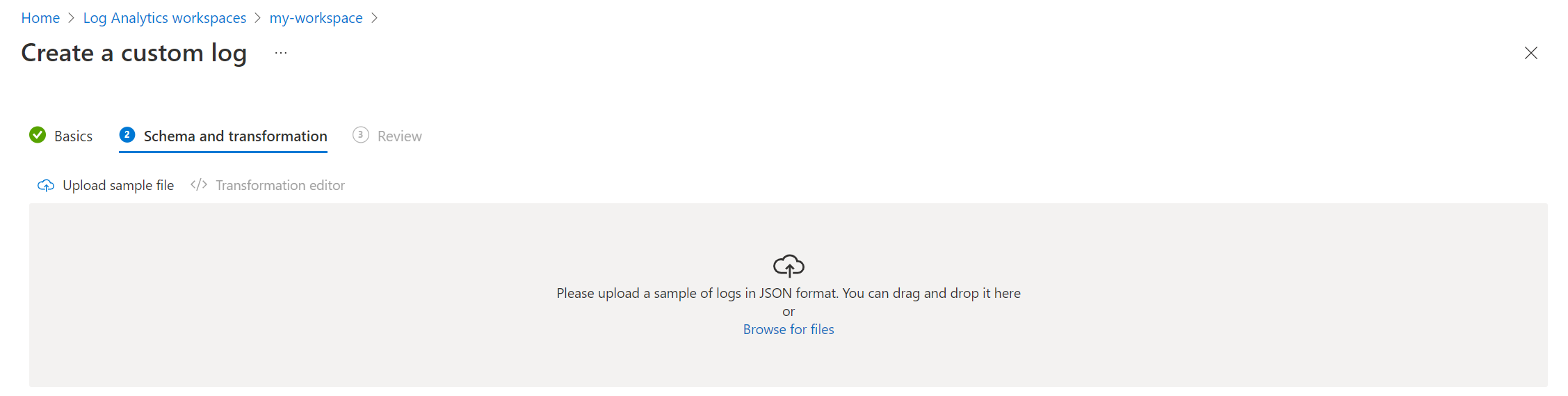
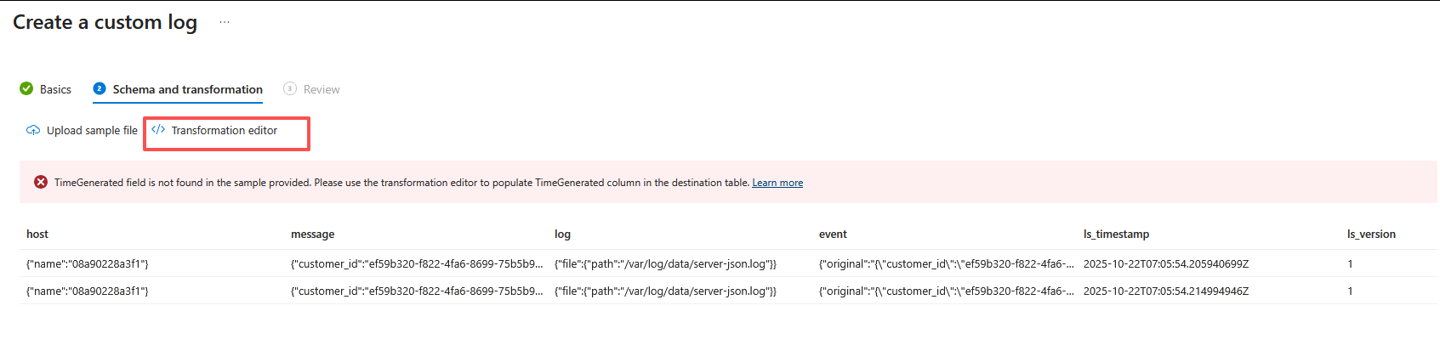
Data from the sample file is displayed with a warning that
TimeGeneratedisn't in the data. All log tables within Azure Monitor Logs are required to have aTimeGeneratedcolumn populated with the timestamp of the logged event. Here, the timestamp of the event is stored in the field calledls_timestamp. You'll add a transformation that will rename this column in the output.Select Transformation editor to open the transformation editor to add this column. You'll add a transformation that will rename this column in the output. The transformation editor lets you create a transformation for the incoming data stream. This is a KQL query that's run against each incoming record. The results of the query will be stored in the destination table.
Add the following query to the transformation editor to add the
TimeGeneratedcolumn to the output:source | extend TimeGenerated = todatetime(ls_timestamp)Select Run to view the results. You can see that the
TimeGeneratedcolumn is now added to the other columns. Most of the interesting data is contained in themessagecolumn, though.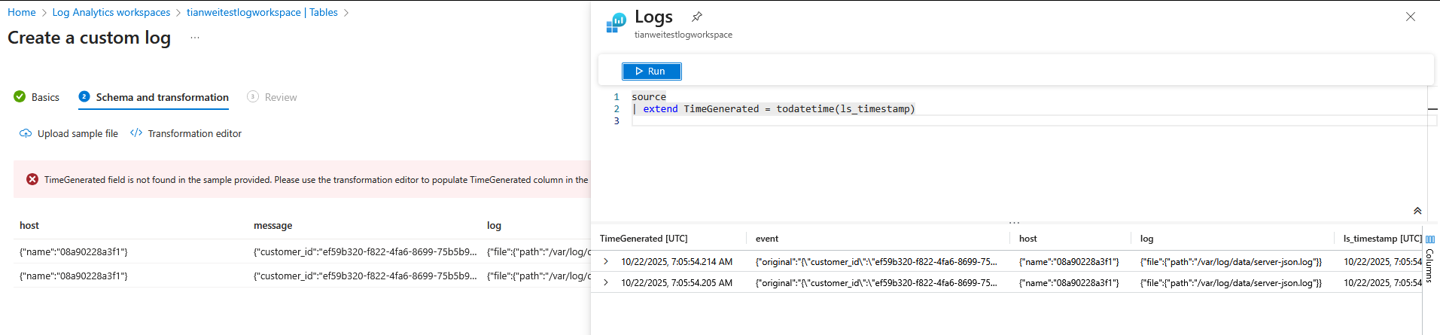
Collect information from the DCR
With the DCR created, you need to collect its information, which is needed in later configuration.
- On the Monitor menu in the Azure portal, select Data collection rules and select the DCR you created. From Overview for the DCR, select JSON View.
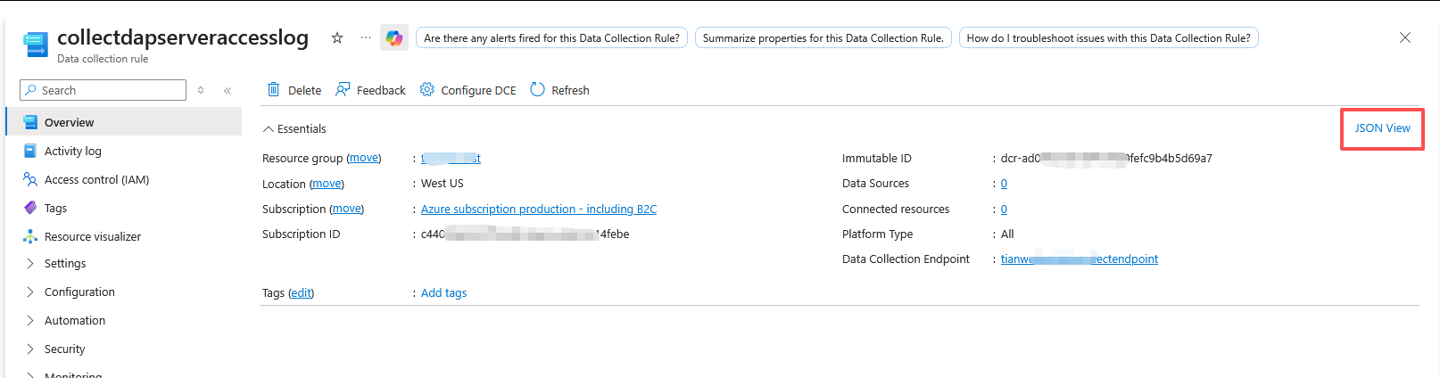
- Copy the values: immutableId and streamDeclarations:

Assign permissions to the DCR
The final step is to give the application permission to use the DCR. Any application that uses the correct application ID and application key can now send data to the new DCE and DCR.
- Select Access Control (IAM) for the DCR and then select Add role assignment.
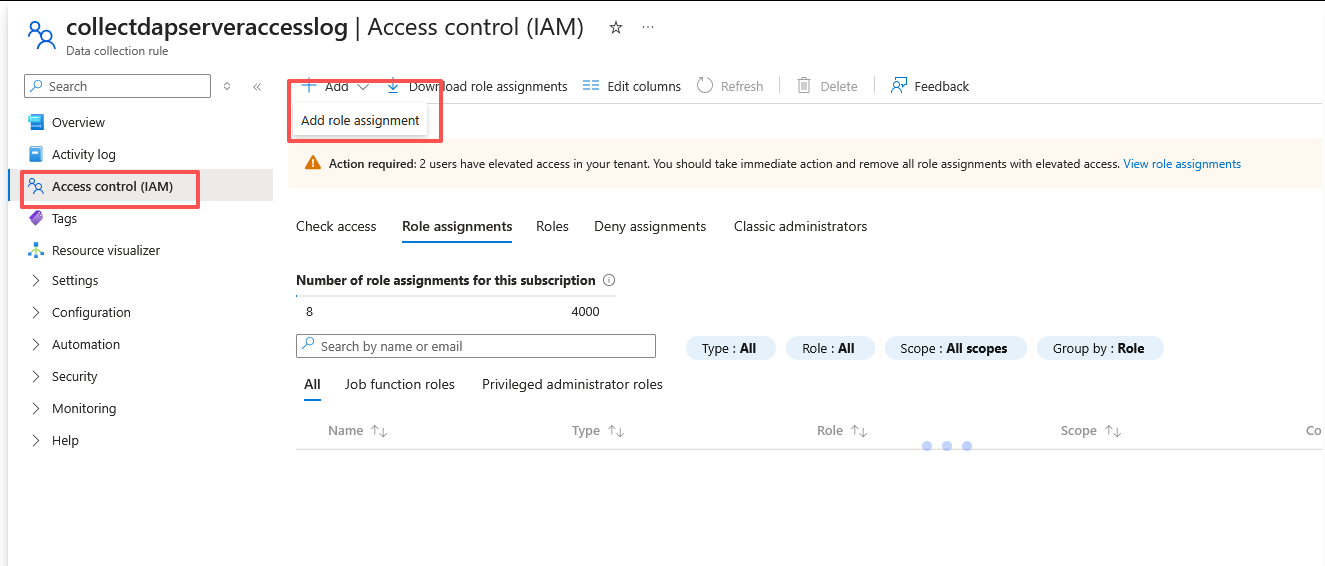
- Select Monitoring Metrics Publisher > Next. You could instead create a custom action with the
Microsoft.Insights/Telemetry/Writedata action.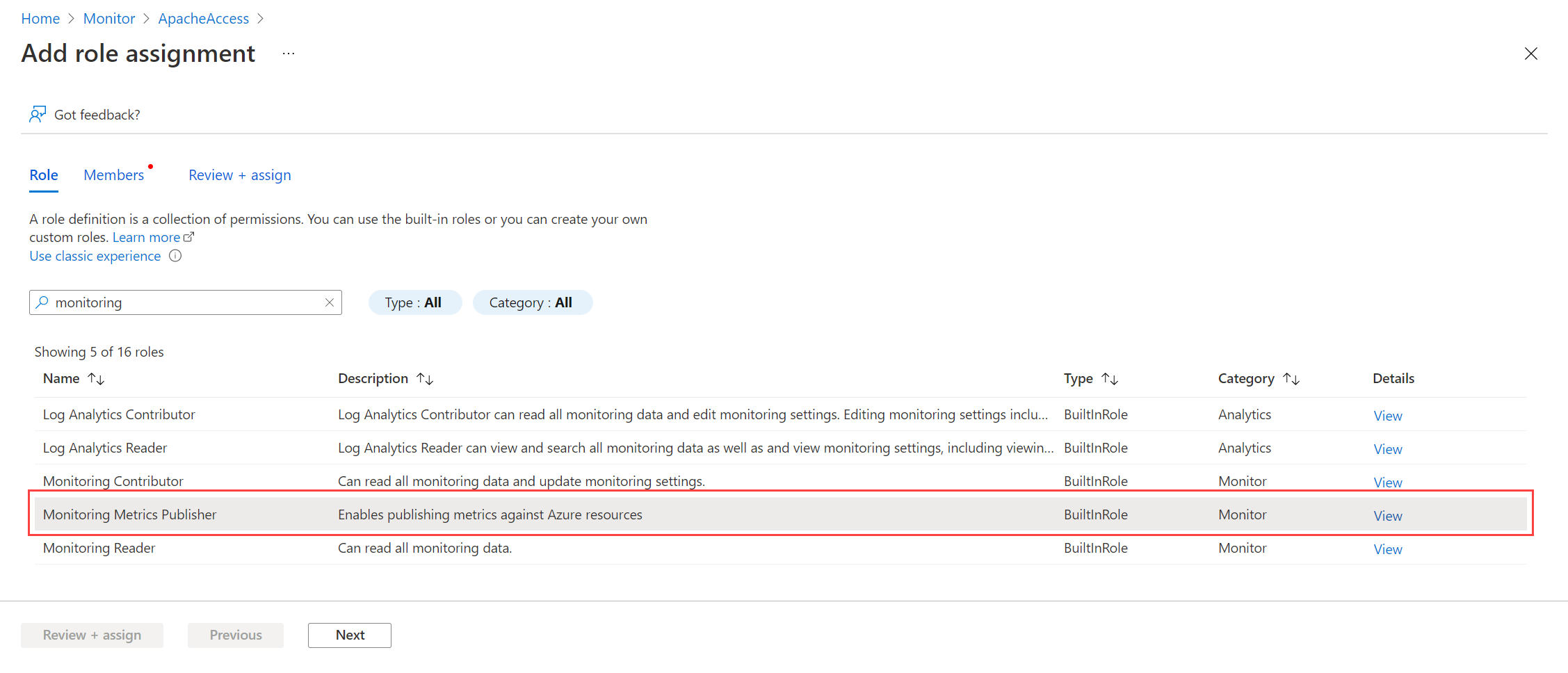
- Select User, group, or service principal for Assign access to and choose Select members. Select the application that you created and then choose Select.

- Select Review + assign and verify the details before you save your role assignment.
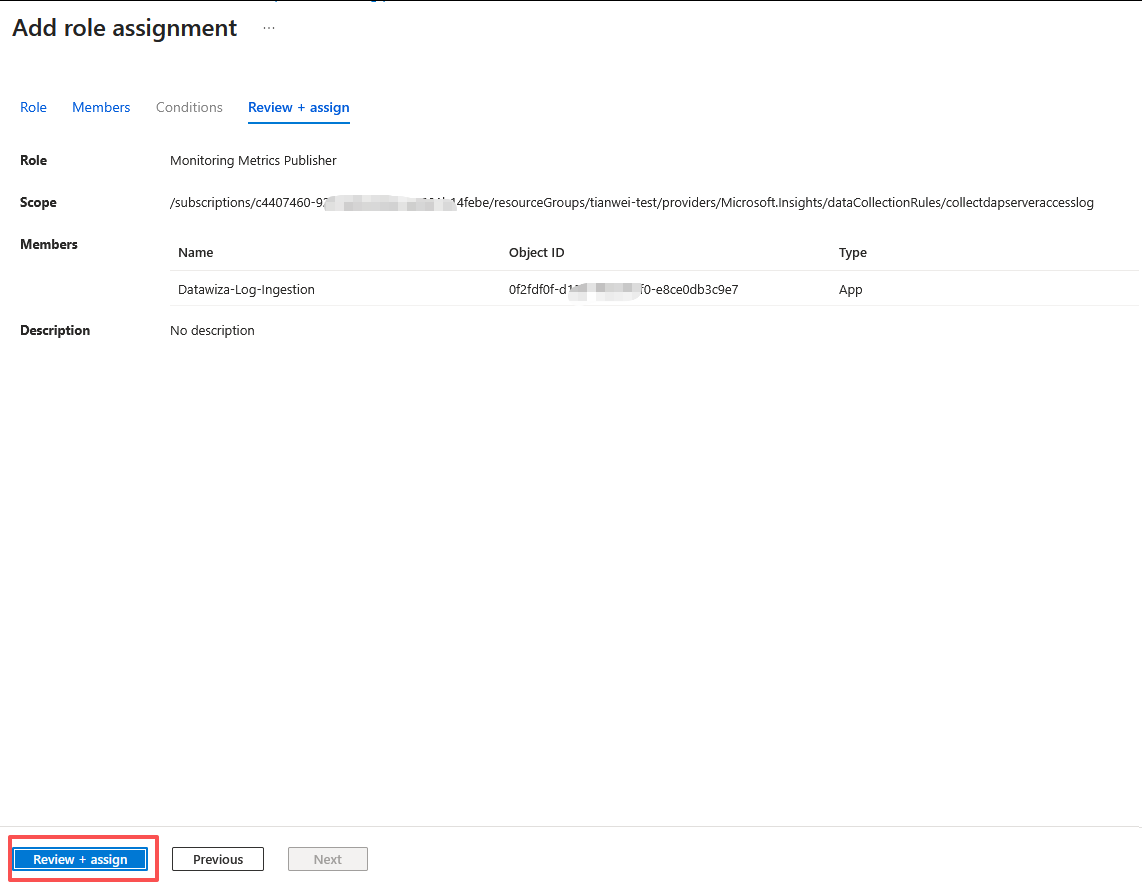
Install Datawiza Sentinel Connector
In the same Docker Compose file on the machine where the Datawiza Access Proxy is installed, add the following configuration block:
datawiza-sentinel-connector:
image: datawiza/dap-sentinel-connector
container_name: datawiza-sentinel-connector
environment:
CLIENT_ID: "{{YOUR_CLIENT_ID}}"
CLIENT_SECRET: "{{YOUR_CLIENT_SECRET}}"
TENANT_ID: "{{YOUR_TENANT_ID}}"
DATA_COLLECTION_ENDPOINT: "{{YOUR_DATA_COLLECTION_ENDPOINT}}"
DCR_IMMUTABLE_ID: "{{YOUR_DCR_IMMUTABLE_ID}}"
DCR_STREAM_NAME: "{{YOUR_DCR_STREAM_NAME}}" # Default is Custom-datawizaserveraccess_CL
volumes:
- ./data:/var/log/datawiza:ro
Replace all values you collected from the previous steps:
- Client ID
- Client Secret
- Tenant ID
- Data Collection Endpoint / Log Ingestion URI
- DCR Immutable ID
- DCR Stream Name
The final docker compose file is like this:
version: '3.8'
services:
datawiza-access-proxy:
image: registry.gitlab.com/datawiza/access-proxy
container_name: datawiza-access-proxy
ports:
- 443:443
restart: always
volumes:
- ./data:/usr/local/openresty/nginx/logs
environment:
PROVISIONING_KEY: {{YOUR_PROVISIONING_KEY}}
PROVISIONING_SECRET: {{PROVISIONING_SECRET}}
datawiza-sentinel-connector:
image: datawiza/dap-sentinel-connector
container_name: datawiza-sentinel-connector
environment:
CLIENT_ID: "{{YOUR_CLIENT_ID}}"
CLIENT_SECRET: "{{YOUR_CLIENT_SECRET}}"
TENANT_ID: "{{YOUR_TENANT_ID}}"
DATA_COLLECTION_ENDPOINT: "{{YOUR_DATA_COLLECTION_ENDPOINT}}"
DCR_IMMUTABLE_ID: "{{YOUR_DCR_IMMUTABLE_ID}}"
DCR_STREAM_NAME: "{{YOUR_DCR_STREAM_NAME}}" # Default is Custom-datawizaserveraccess_CL
volumes:
- ./data:/var/log/datawiza:ro
To test the log sending feature without a running Datawiza Access Proxy, you can download our sample log file and place it in the ./data directory.
Validate Log Delivery
After configuring log forwarding, you can validate the delivery in Log Analytics: 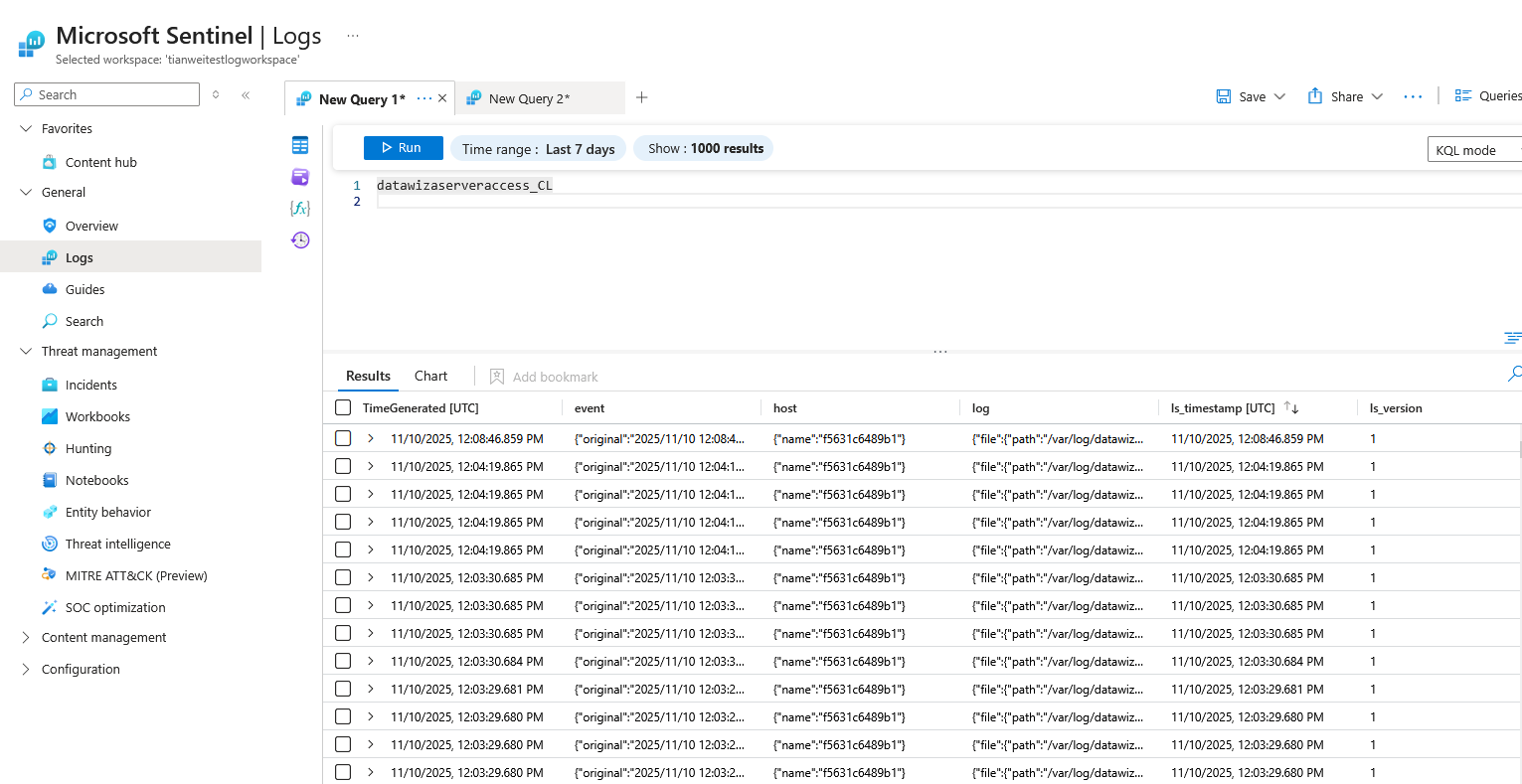
Conclusion
By integrating Datawiza Access Proxy with Microsoft Sentinel, organizations can enhance their security posture with real-time monitoring and analytics. Ensure all configurations are correctly set up to enable seamless log forwarding and analysis.
