Architecture
System Architecture
Datawiza Access Proxy (DAP) is an identity-aware reverse proxy sitting in front of applications. The traffic to applications reaches DAP first, and then is proxied to applications if it's allowed by the access policies. The following diagram illustrates a typical architecture when deploying DAP.
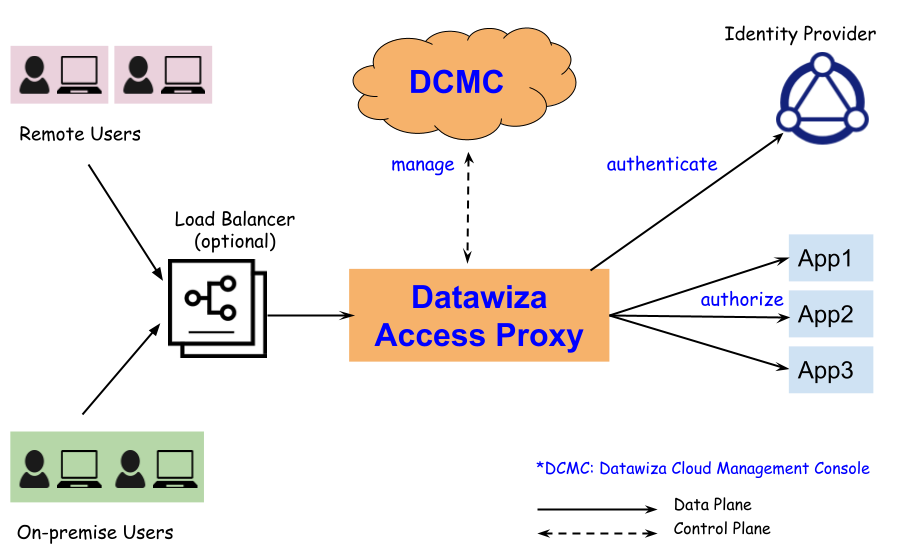 DAP is managed by a centralized cloud-based management console: Datawiza Cloud Management Console (DCMC). DCMC provides UI and Restful APIs for administrators to manage the configurations of DAP and its access control policies. No matter DAPs are deployed in AWS, GCP, Azure or on-premise, all of them can be managed by the single DCMC.
DAP is managed by a centralized cloud-based management console: Datawiza Cloud Management Console (DCMC). DCMC provides UI and Restful APIs for administrators to manage the configurations of DAP and its access control policies. No matter DAPs are deployed in AWS, GCP, Azure or on-premise, all of them can be managed by the single DCMC.
Deploy Modes
DAP can be deployed via the following two modes:
- Sidecar mode. DAP is deployed on the same server or Kubernetes Pod where the application resides. DAP proxies traffic to applications via localhost.
- Standalone mode. DAP is deployed on a different server than where the application resides.
Under both deploy modes, make sure your application only allows the traffic from DAP to access. Otherwise others may circumvent DAP to access application directly. For sidecar mode, only allow your application listening to localhost; for standalone mode, only allow your application accepting traffic from the IPs of DAP services.
You can deploy multiple DABs for your applications. For example, you have your application running on server 1 and server 2. Using the sidecar mode, you may deploy one DAP on server 1 and another DAP on server 2.
