FAQ
Frequently Asked Questions
- Frequently Asked Questions
- How many deployments/applications/IdPs can I have?
- For the same deployment, can I have multiple applications?
- For the same application, can I have multiple DAPs connected to one IdP instance?
- Can I configure different IdPs for the same application?
- What is the difference between the Listen Port and the port of Application URL?
- The APP logout and IdP logout
- Provisioning Key and Secret
- How to invite co-workers to the organization
How many deployments/applications/IdPs can I have?
You can find the limits in your plan details (Click the Plan in the left-hand navigation bar). 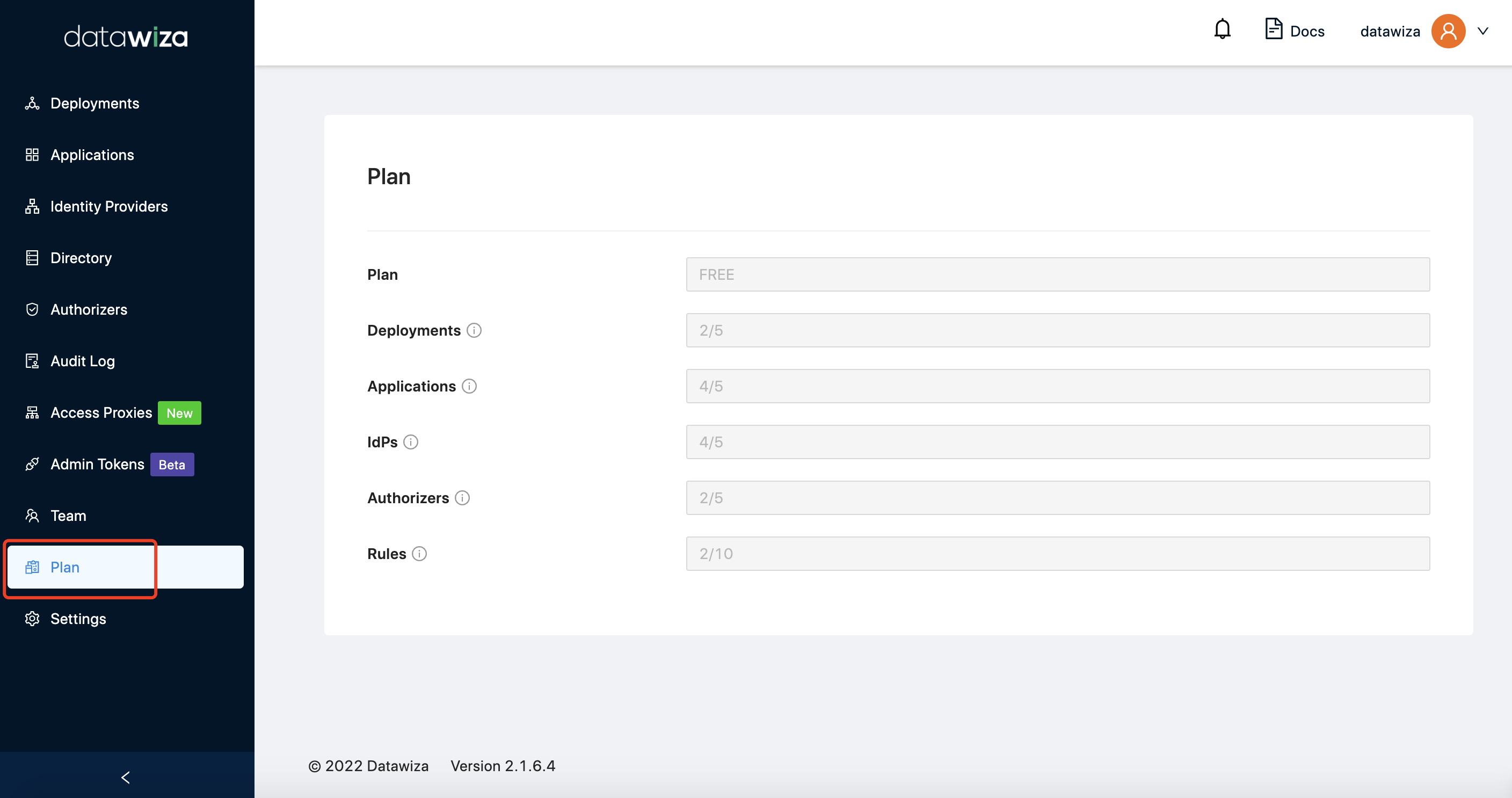 For free license, the default limit is 2 deployments, 5 applications, 5 IdP settings, 5 authorizers, 10 access policies.
For free license, the default limit is 2 deployments, 5 applications, 5 IdP settings, 5 authorizers, 10 access policies.
For the same deployment, can I have multiple applications?
Yes, you can have multiple applications for one deployment.
For the same application, can I have multiple DAPs connected to one IdP instance?
Yes, you can have multiple DAPs for one application and they can connect to the same IdP instance.
Can I configure different IdPs for the same application?
Yes, you can configure different IdPs for the same application. The end user will have an UI to choose which IdP to log in with.
What is the difference between the Listen Port and the port of Application URL?
The Listen Port is the port that DAP listens on, while the port of Application URL is the port that customers or end users should access. In general, if you have a load balancer fronting the AP, the two ports can be different. If you expose the DAP to the public directly, these two ports refer to the same port.
The APP logout and IdP logout
By default, the DAP will only log out the application, which means you will not need to re-enter the username/password to log in the application again. And other apps you logged in will not log out. You can find this option Single Sign Out, in Application -> Advanced -> Advanced Options: 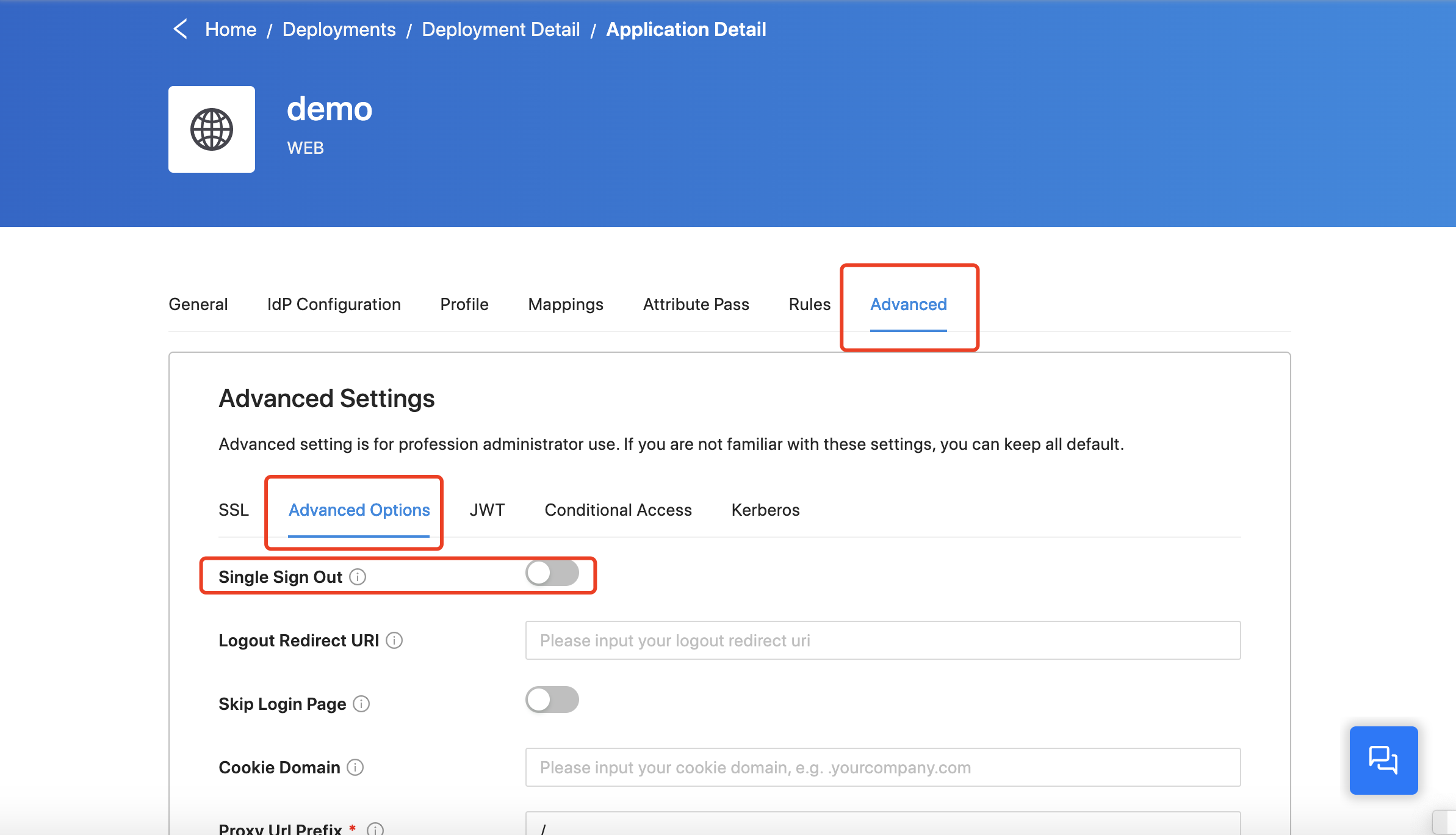
If you enable this option, the DAP will sign out your Identity Provider at the same time when it signs out the application. In this situation, any other service you logged in with the same account will log out.
For example, we assume you have the Google social account as the IdP for DAP and you have logged in the DAP and Gmail. You will only log out the DAP but not Gmail when you disable the Single Sign Out. And you will log out the DAP and Gmail when you enable this option.
Provisioning Key and Secret
By default, the provisioning key and secret have an expiration time of another month which will extend for one month automatically every ten minutes if your DAP is online. So you don't need to worry about that if your DAP is always online. Also, you can always create a new pair of provisioning key and secret in Provisioning Keys tab of your deployment.
How to invite co-workers to the organization
Non-Azure AD accounts
For non-Azure AD accounts, when users with the same email domain register, each of them will have a separate organization. You need to invite your co-workers if you want to share them with the same organization: Select Team tab, click Invite Member: 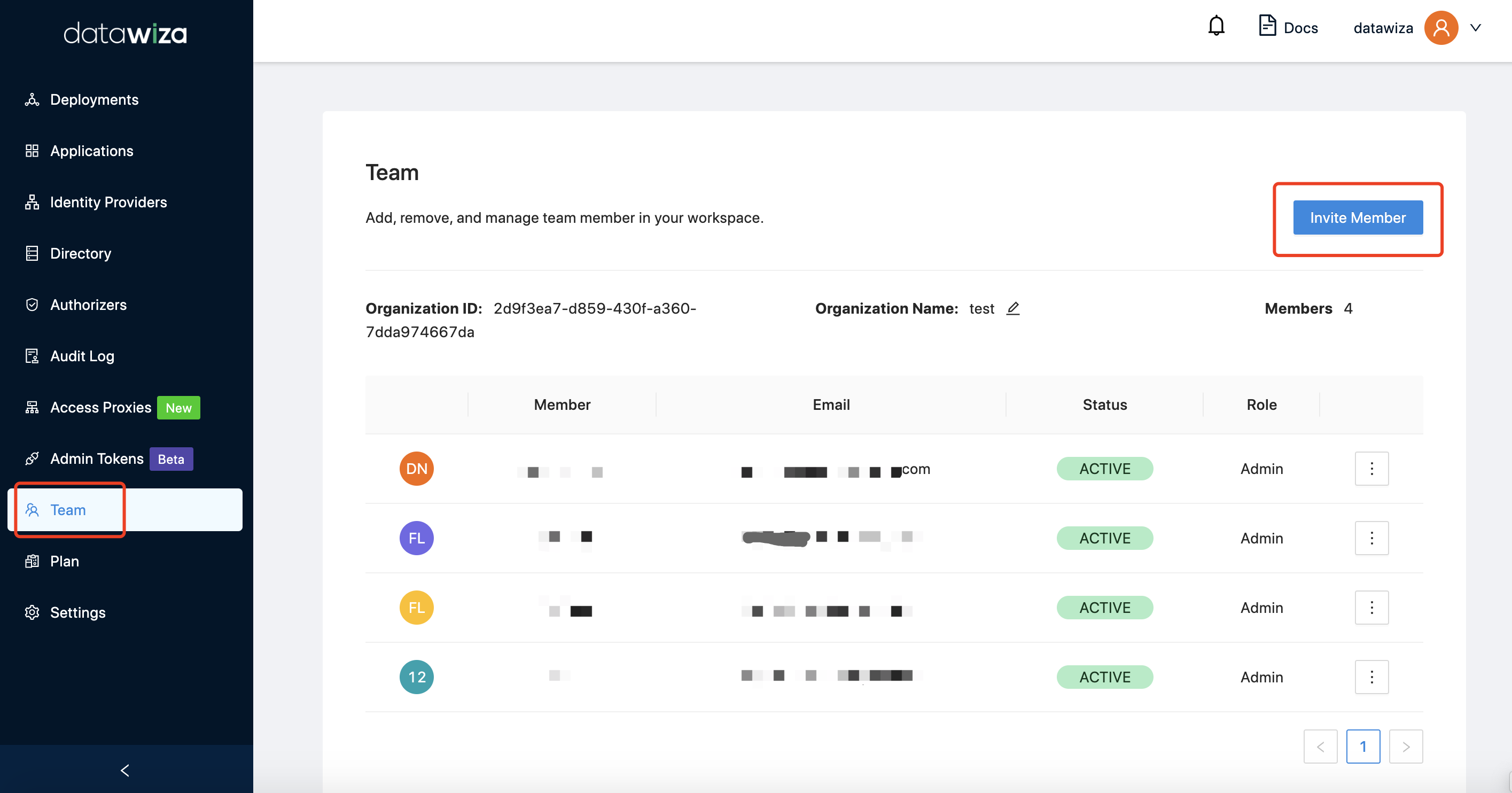 Input the basic information:
Input the basic information: 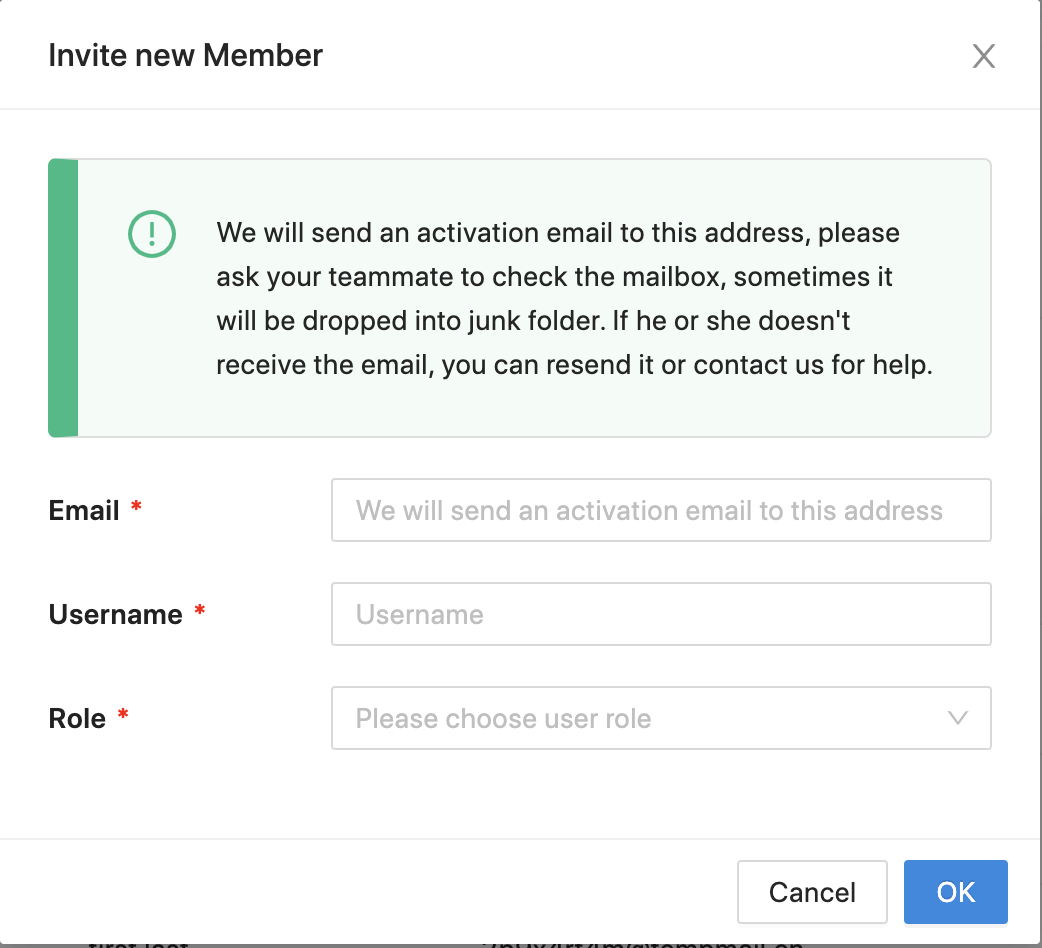 Then we will send the invite email to the user. Click
Then we will send the invite email to the user. Click Activate Account in your invite email: 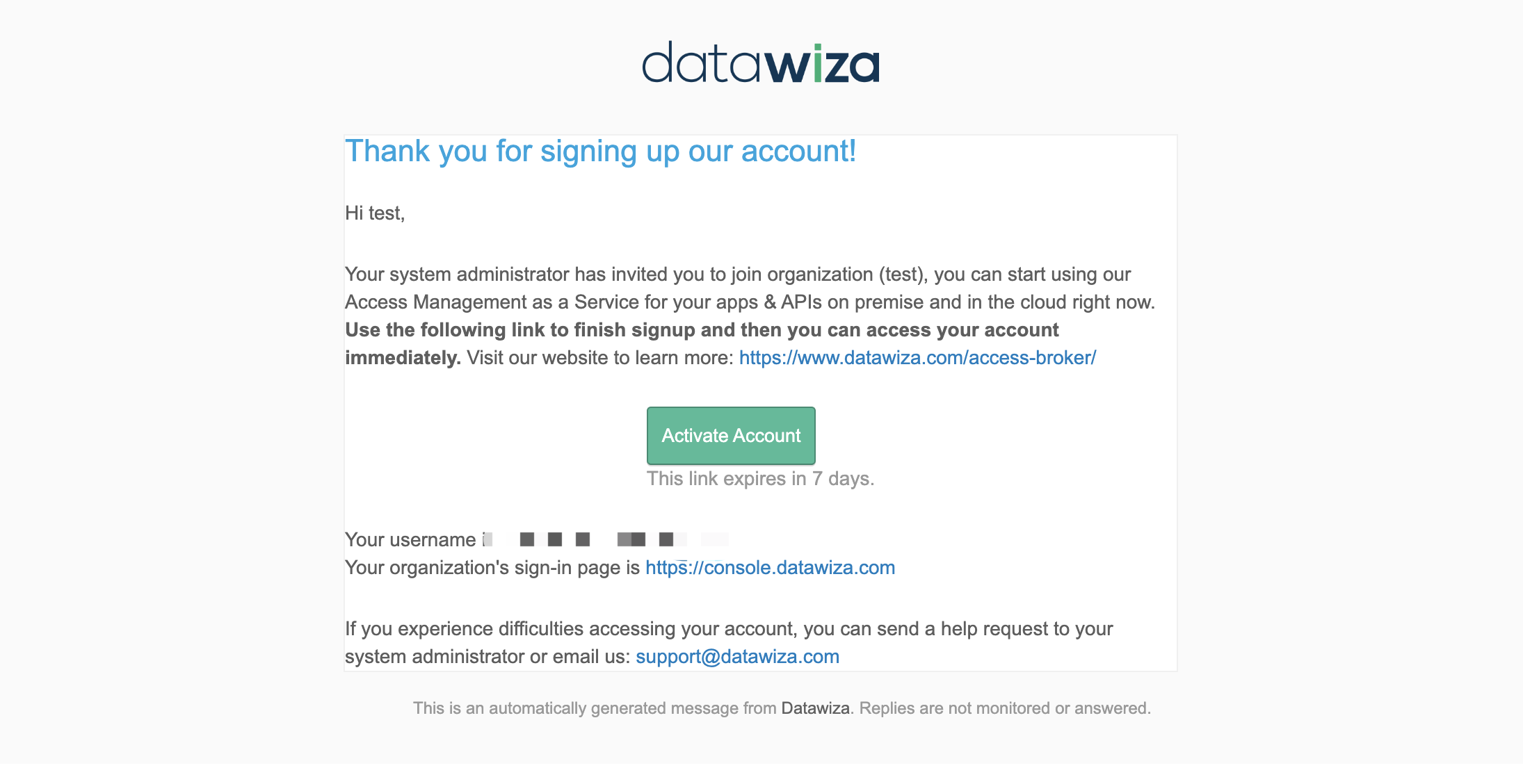 Input the basic information and click
Input the basic information and click Sign up and Join: 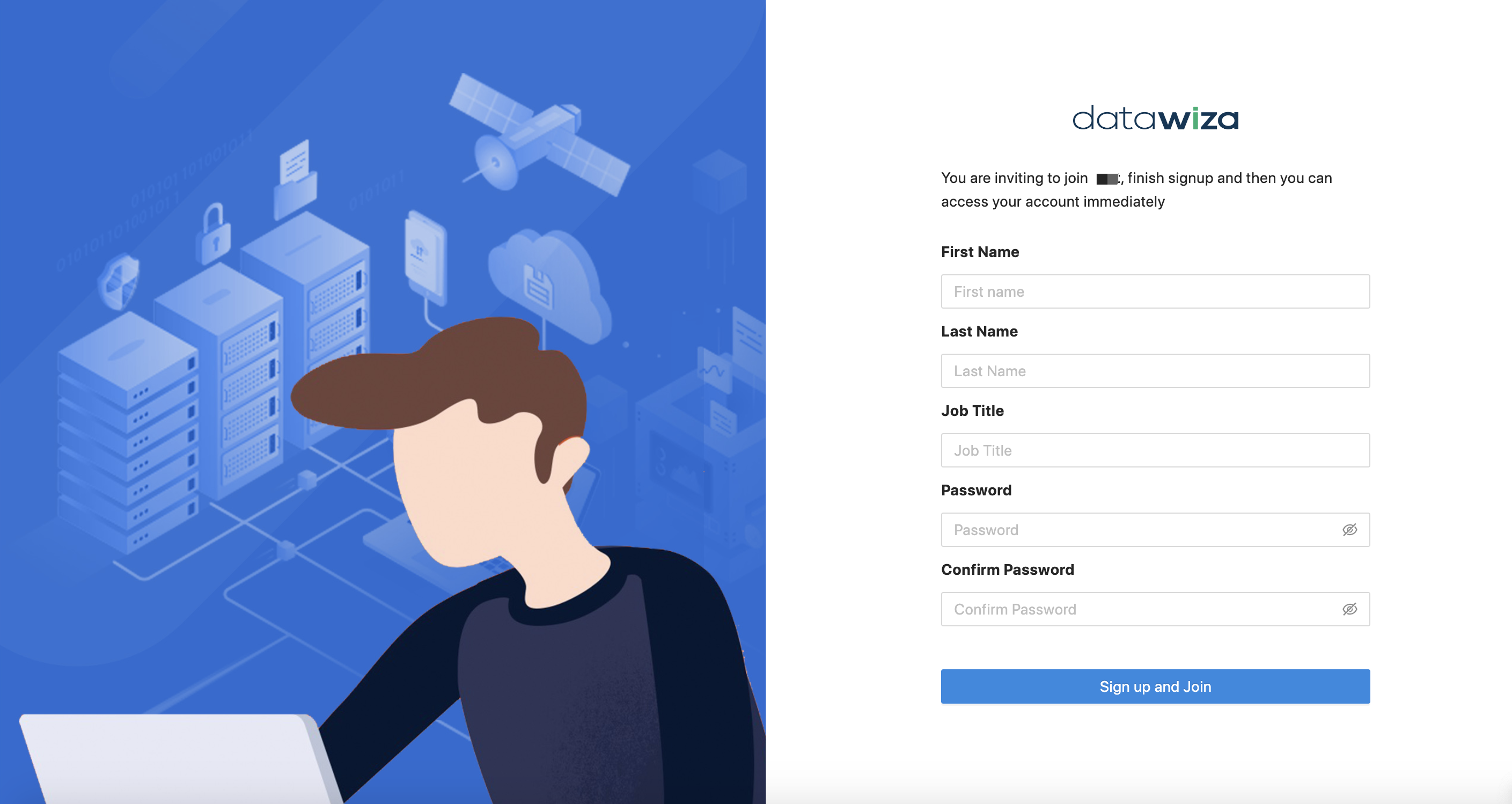 Then you will be redirected to the DCMC login page and the user will be in your organization:
Then you will be redirected to the DCMC login page and the user will be in your organization: 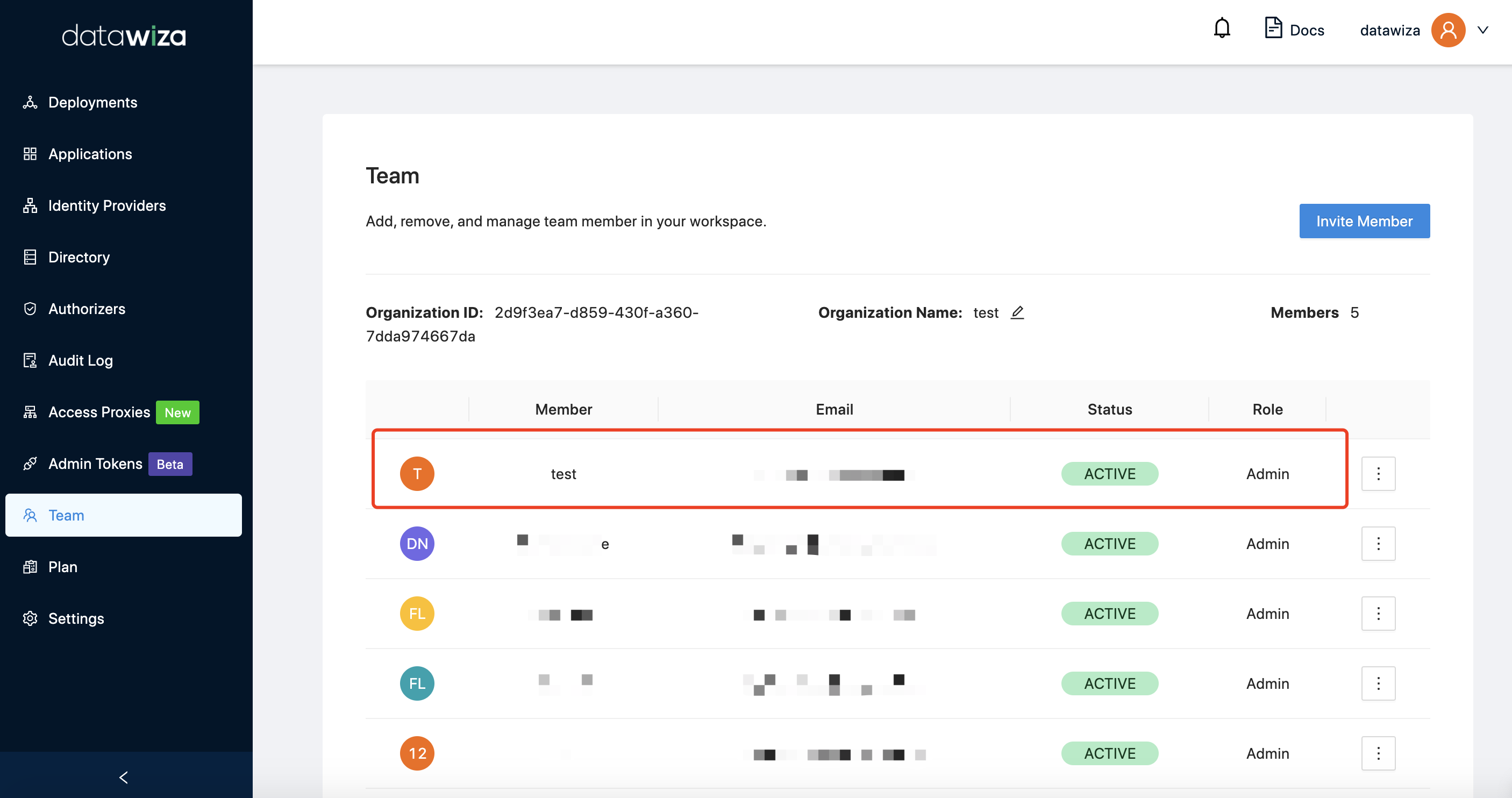
Azure AD accounts
If you registered DCMC with Azure AD account, users in the same tenant will be put in the same organization by default. If you want to restrict access to DCMC, you can configure it in Azure portal: Go to Azure portal and find the Datawiza Management Console in Enterprise applications: 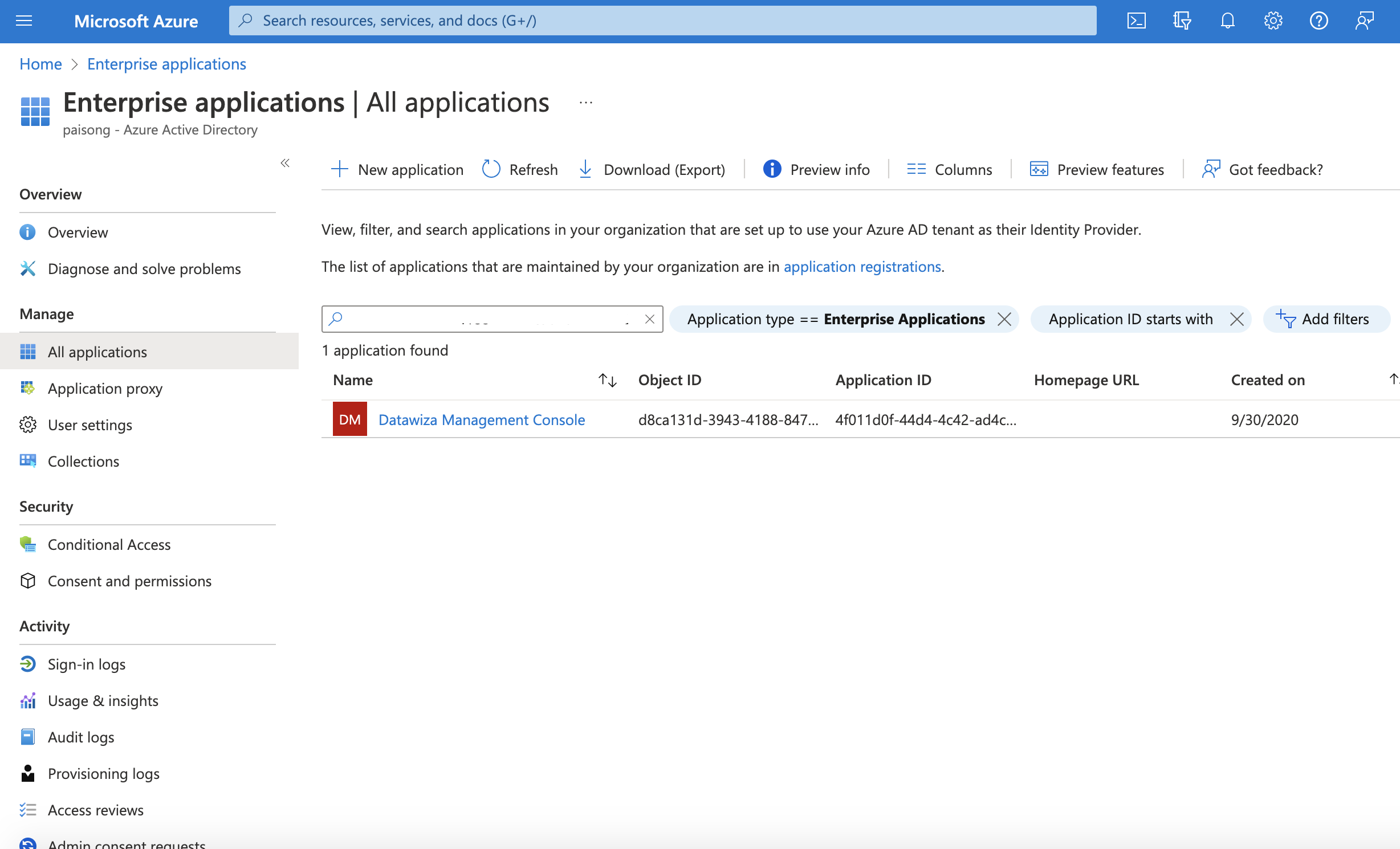 Select
Select Properties, and enable the Assignment required. Then users and other apps or services must first be assigned this application before being able to access it. 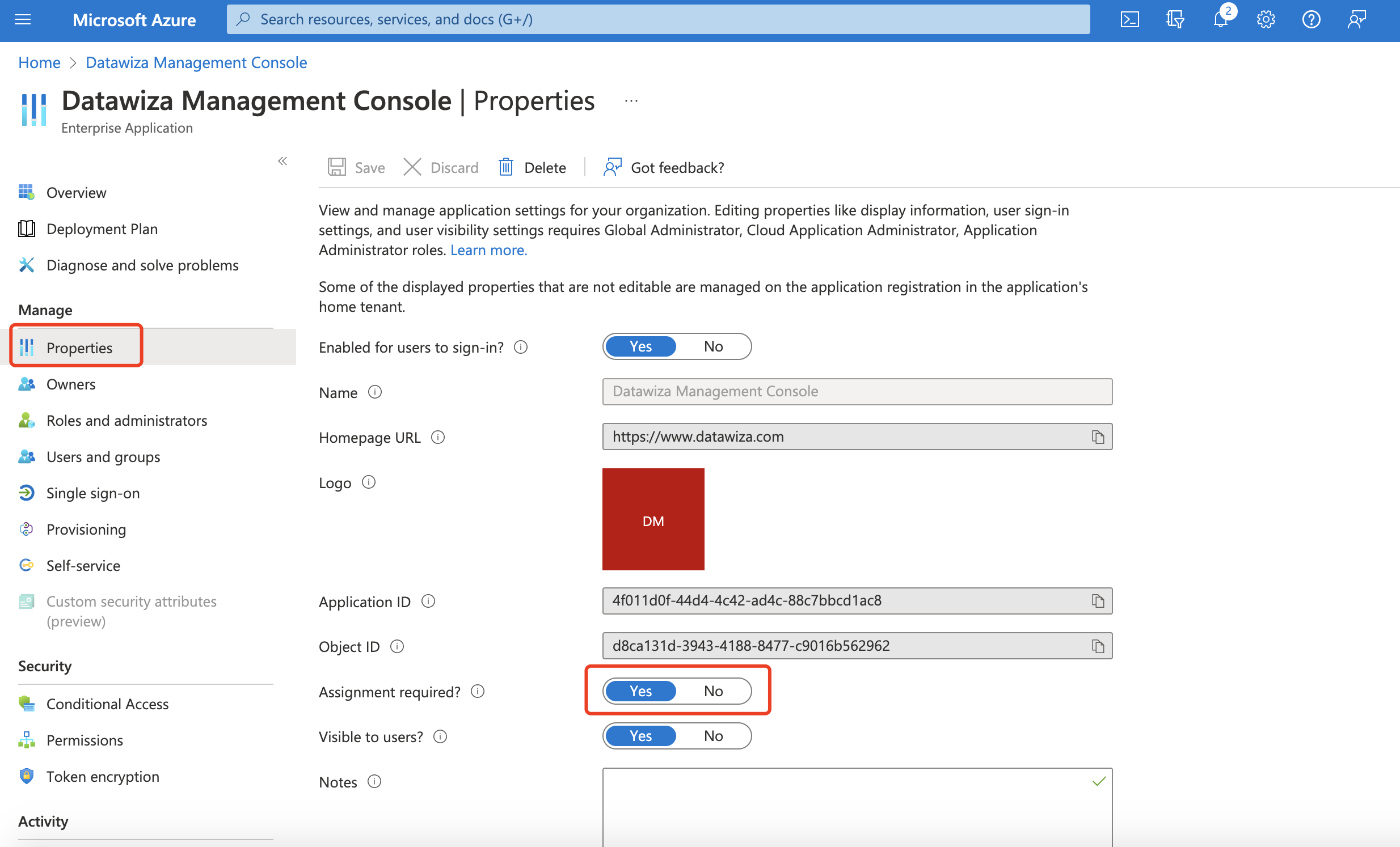 The user without the access will be shown the Azure error page if they login to the DCMC:
The user without the access will be shown the Azure error page if they login to the DCMC: 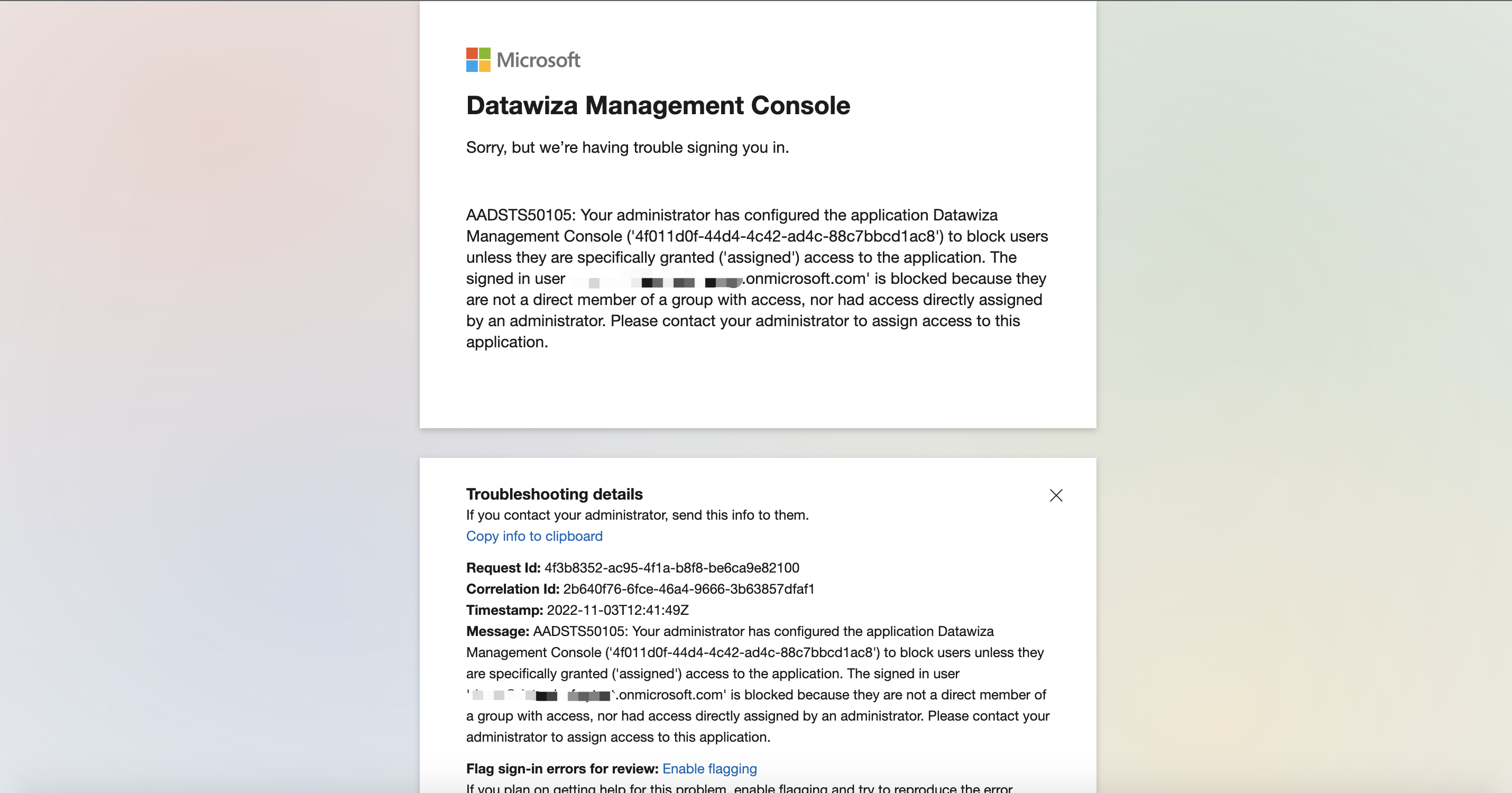 Now we need to config who should have the access to the DCMC. Back to Azure portal, go to
Now we need to config who should have the access to the DCMC. Back to Azure portal, go to Users and groups, click + Add user/group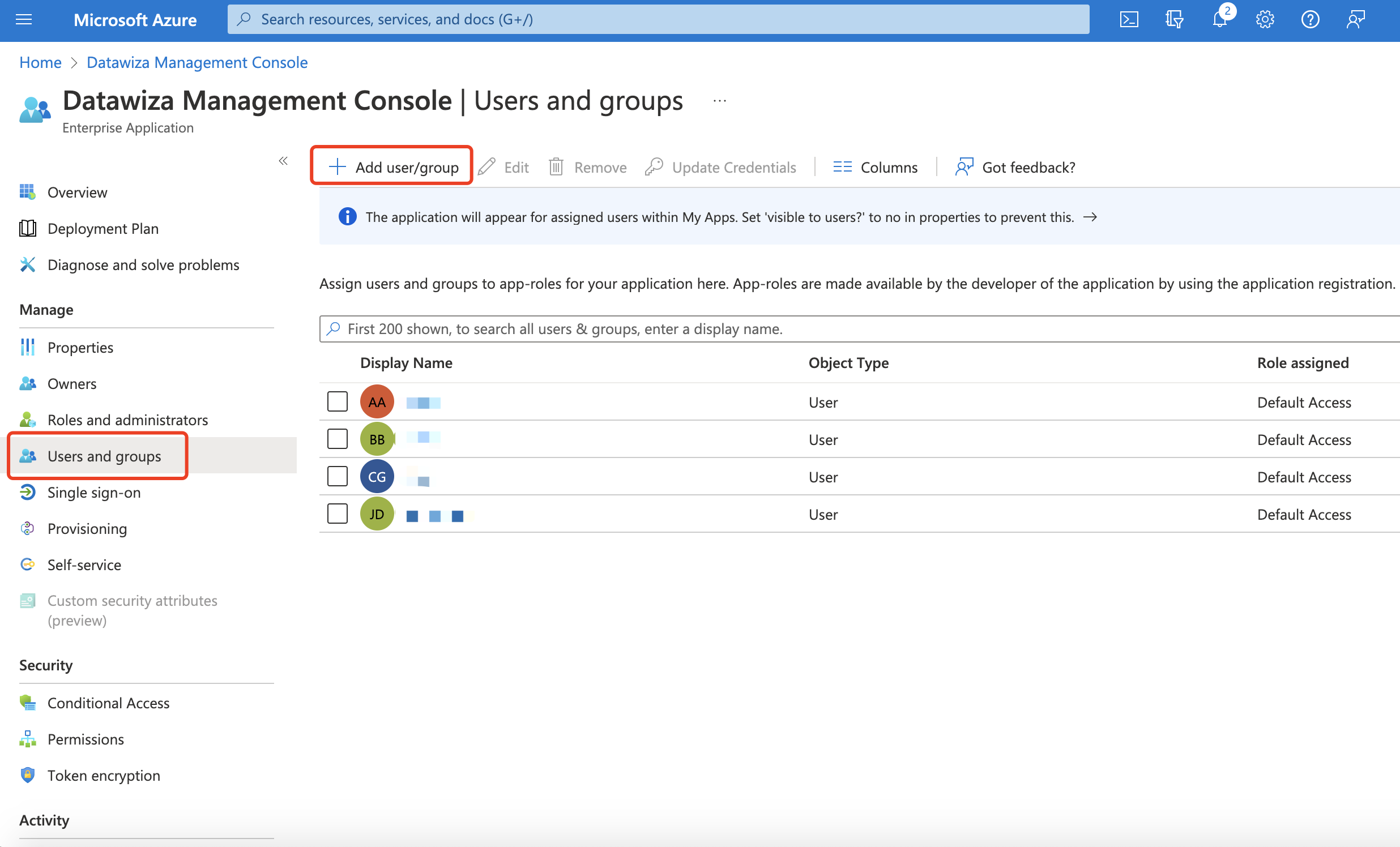 Assign the users:
Assign the users: 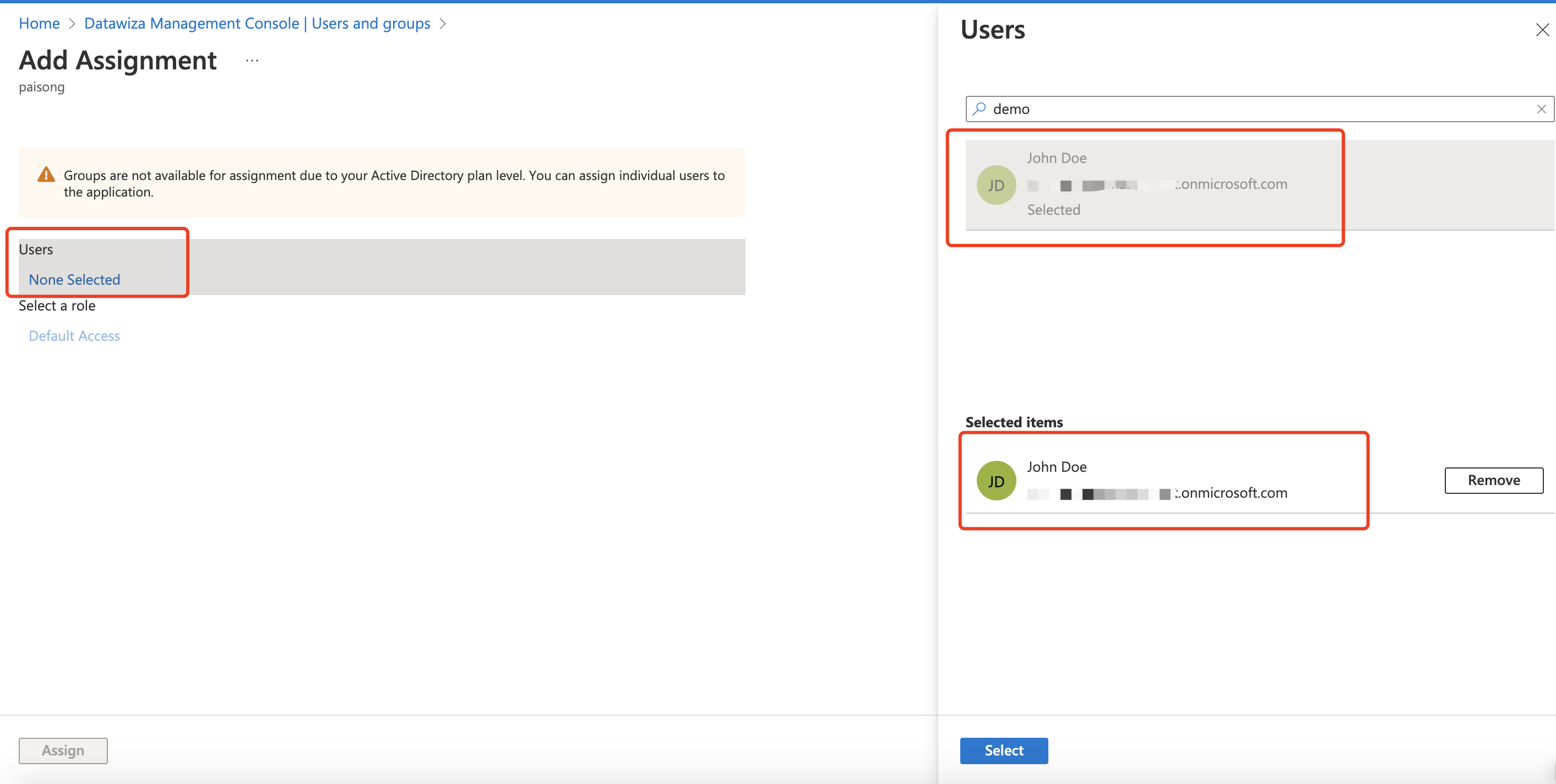 Then, only the users here can log into the DCMC with Azure AD account.
Then, only the users here can log into the DCMC with Azure AD account.
