Enable Microsoft Entra ID (Azure AD) SSO and MFA to Oracle JDE via Datawiza
Overview
This tutorial shows how to enable Microsoft Entra ID (Azure Active Directory (AD)) SSO and MFA for Oracle JD Edwards (JDE) via Datawiza. Learn more about enabling SSO and MFA for Oracle JD Edwards (JDE) with Datawiza.
The benefits of integrating applications with Microsoft Entra ID via Datawiza includes:
- Improved Zero Trust security through Microsoft Entra ID SSO, MFA and Conditional Access
- No-Code easy integration between Microsoft Entra ID and any web applications, including JDE, E-Business Suite, Sibel, Peoplesoft and homegrown apps
- A single control plane, Datawiza Cloud Manage Console, to manage access to applications in public clouds and on-premise
Background
This document focuses on solving the problem when modern identity providers integrate with the legacy Oracle JDE application. We accomplish the integration based on the fact that JDE supports HTTP Authorization Headers.
In many cases, legacy applications have great difficulty integrating with modern SSO, mainly due to the absence of modern protocol support.
The Datawiza no-code solution effectively reduces the cost of integration, overcomes the gap, and significantly improves application security.
Architecture
The solution contains the following components:
- Identity Provider (IdP): For demonstration purpose, we use Microsoft Entra ID, Microsoft's cloud-based identity and access management service, which helps users sign in and access external and internal resources.
- Oracle JDE Application: The legacy application to be protected by Datawiza and integrated with Microsoft Entra ID SSO & MFA.
- Datawiza Access Proxy (DAP): A super lightweight container-based reverse-proxy implements OIDC/OAuth or SAML for user sign-on flow and transparently passes identity to applications through HTTP headers.
- Datawiza Cloud Management Console (DCMC): A centralized management console that manages DAP. DCMC provides UI and RESTful APIs for administrators to manage the configurations of DAP and its granular access control policies.
Both SP initiated flow and IdP initiated flow are supported by the architecture discussed here. Below we will use SP initiated flow for demonstration purposes.
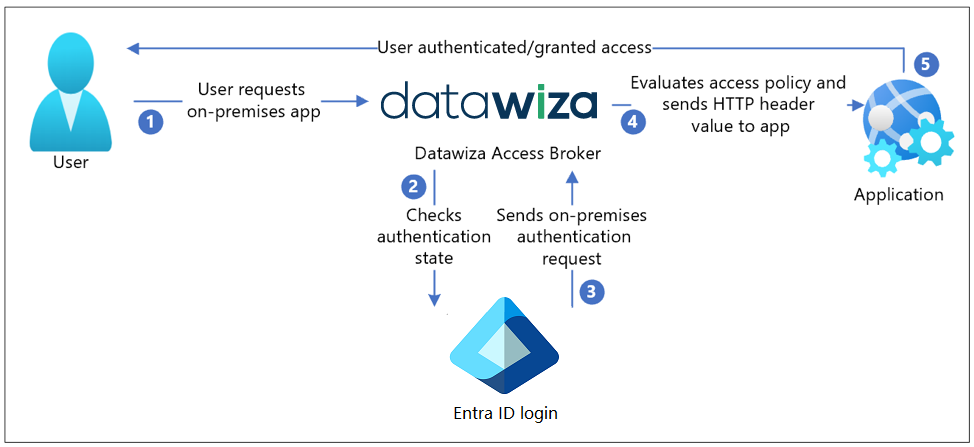
Steps Description
- The user accesses the application URL, which hits the DAP;
- The DAP checks the user's authentication state. If it doesn't receive a session token, or the supplied session token is invalid, then it redirects the user to Microsoft Entra ID (OIDC IdP in this example, you can use SAML IdP as well);
- Microsoft Entra ID pre-authenticates user and applies any enforced Conditional Access policies, and then the user is redirected back to DAP and SSO is performed using issued OIDC token;
- The DAP evaluates its own access policies and generates attribute values to be included in HTTP headers and forwarded to the application. During this step, the DAP may call out to the identity provider to retrieve the information needed to set the header values correctly. The DAP then sets the header values and sends the request to the application;
- The user is now authenticated and has access to the application.
Prerequisites
Prior Datawiza Access Proxy experience isn't necessary, but you need:
- An Azure subscription. If you don't have a subscription, you can get a trial account
- A Microsoft Entra ID tenant that's linked to your Azure subscription
- Docker and docker-compose are required to run DAP
- User identities synchronized from an on-premises directory to Microsoft Entra ID or created directly within Microsoft Entra ID and flowed back to your on-premises directory
- An account with Microsoft Entra ID application admin permissions
- (Optional) An SSL Web certificate for publishing services over HTTPS, or use default Datawiza self-signed certs while testing
- An existing Oracle JDE environment. Supported versions include: v9.0 or later.
Getting started with Datawiza
To integrate JDE, login to Datawiza Cloud Management Console (DCMC).
Welcome to the DCMC homepage! Let's get started:
Click the orange Getting started button, which will guide you through the configuration steps.
Specify a Name and a Description, and click Next.
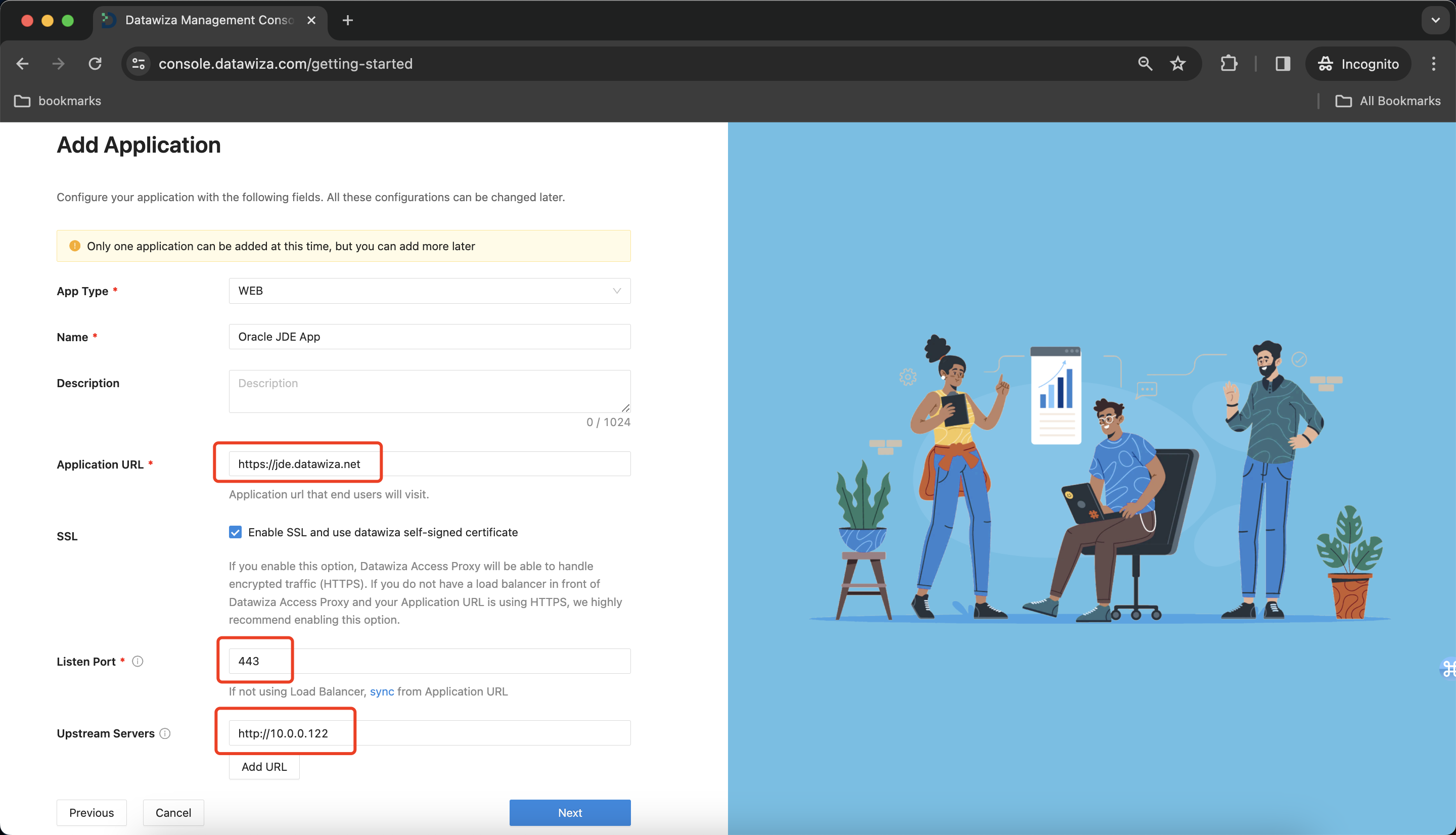
Add Application
Configure your application with the following values:
| Property | Value |
|---|---|
| App Type | Since JDE is a web application, select WEB here. |
| Name | The name of your application. Put a meaningful name here. I use the Oracle JDE App. |
| Application URL | The external facing URL of the application. For example https://jde-external.example.com. You can use localhost DNS for testing purposes. I use https://jde.datawiza.net. |
| Listen Port | This is the port that the Datawiza Access Proxy listens on. For simplicity, you can use the same port as the one in Public Domain above if you are not deploying the Datawiza Access Proxy behind a Load Balancer. |
| Upstream Servers | The URL and port combination of the Oracle JD Edwards Implementation is being protected. Mine is https://10.0.0.122:8080. |
Select Next.
Configure Identity Provider
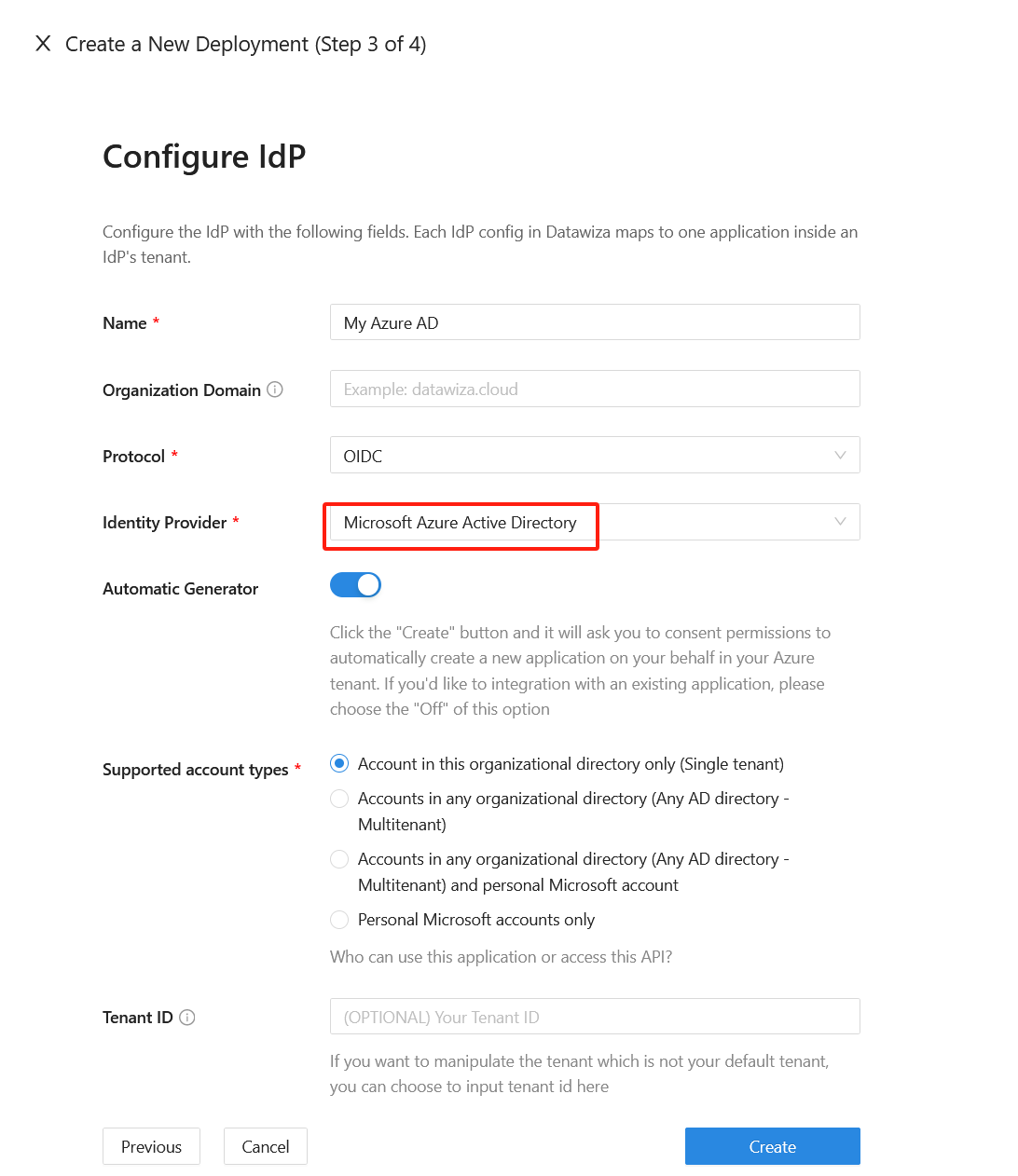
On the Configure IdP dialog, enter the relevant information.
Info
DCMC has one-click integration to help complete Microsoft Entra ID configuration. DCMC calls the Microsoft Graph API to create an application registration on your behalf in your Microsoft Entra ID tenant.
Select Create.
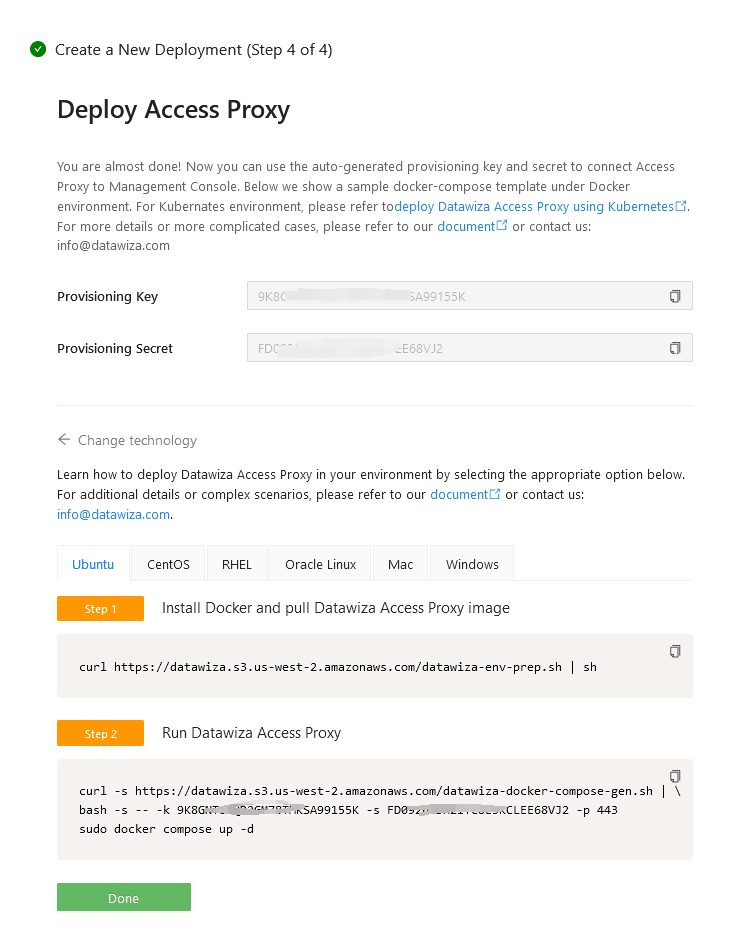
Install and run Datawiza Access Proxy
Once clicking on the Create button, the basic configuration on the management console is finished. You will see the final step of the guide, which presents you with a page showing the simple steps to deploy Datawiza Access Proxy (DAP) with your application. Note down the commands for your deployment. The first command will download Docker and Datawiza Access Proxy image, and the second command will create a Docker Compose file and run Datawiza Access Proxy. You can refer to Install and Run Datawiza Access Proxy by command for more information.
Single Sign-On & HTTP Headers
The DAP gets user attributes from IdP and passes them to the upstream application via header or cookie.
In order to let the Oracle JDE application recognize the user correctly, there is one more step to configure, which instructs DAP to pass the values from the identity provider to the application under what name through HTTP header.
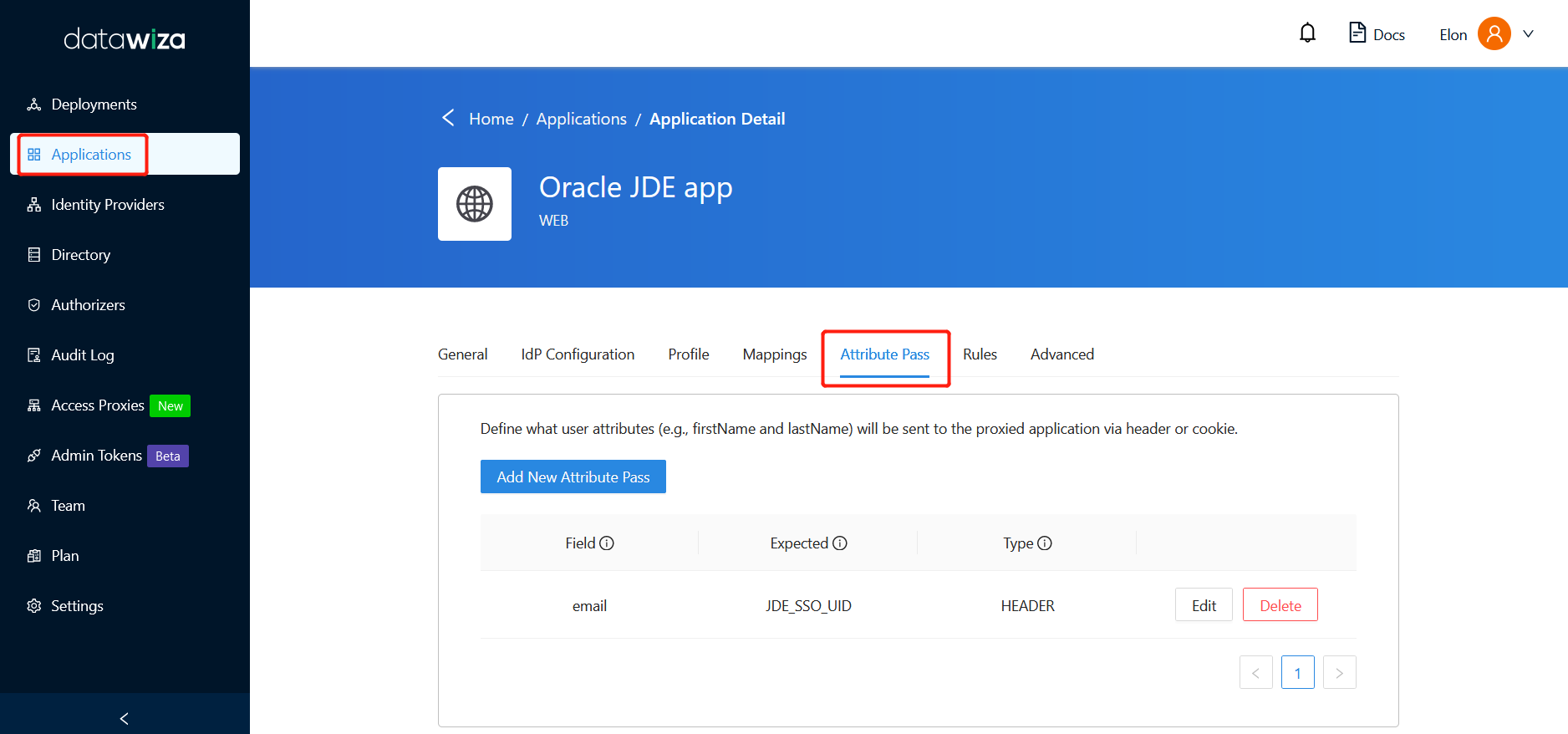
Such configuration will be done in the Applications tab on the left panel and go to Attribute Pass sub-tab.
For Oracle JDE, please refer to the screenshot below to configure the attribute pass:
- Field: email
- Expected: JDE_SSO_UID
- Type: HEADER
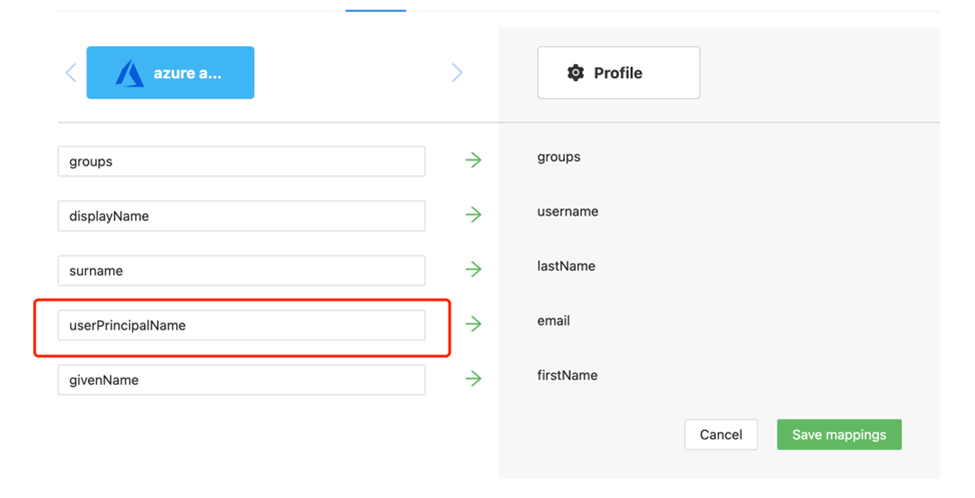
Info
This configuration will use user principal name as the login username for JDE. You can also specify user's other identity information as the login username in the Mappings tab.
SSL Configuration
- Certificate Configuration: Select Advanced tab in your application page:
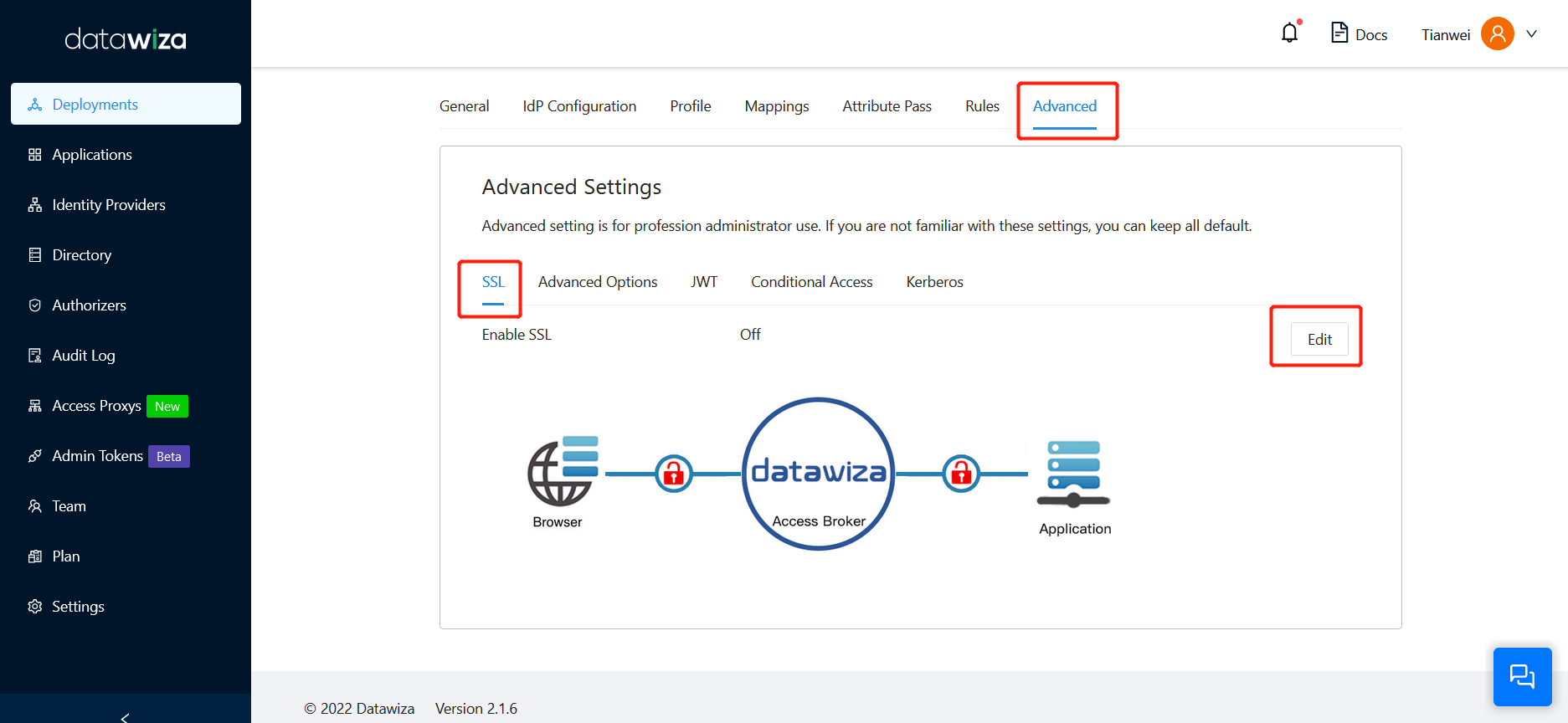
- Enable SSL and select a proper Cert Type.
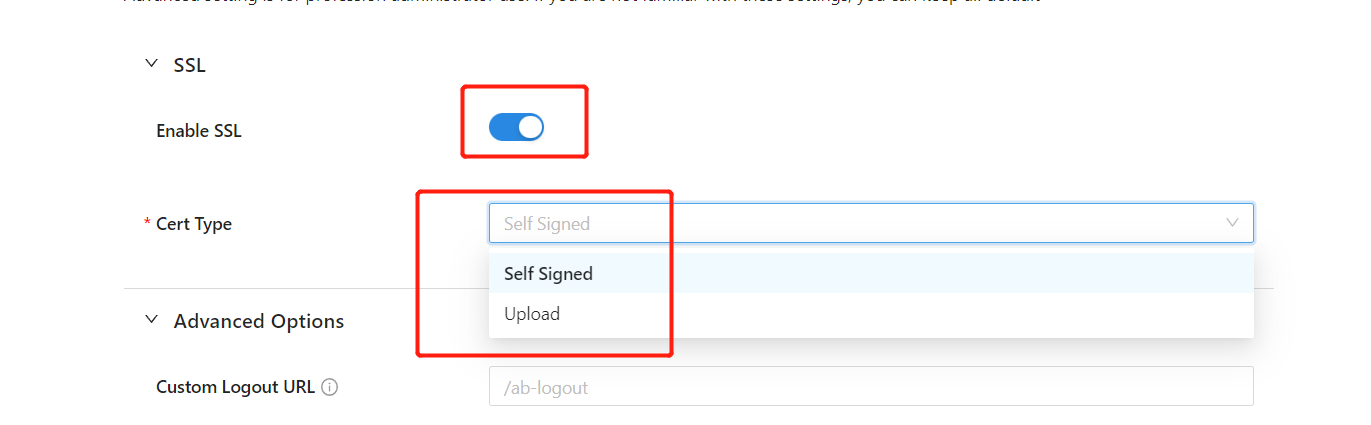
- We provide a self-signed certificate for localhost. It can be used for testing purposes.
- Optionally, you can choose to upload your own certificate from a file:
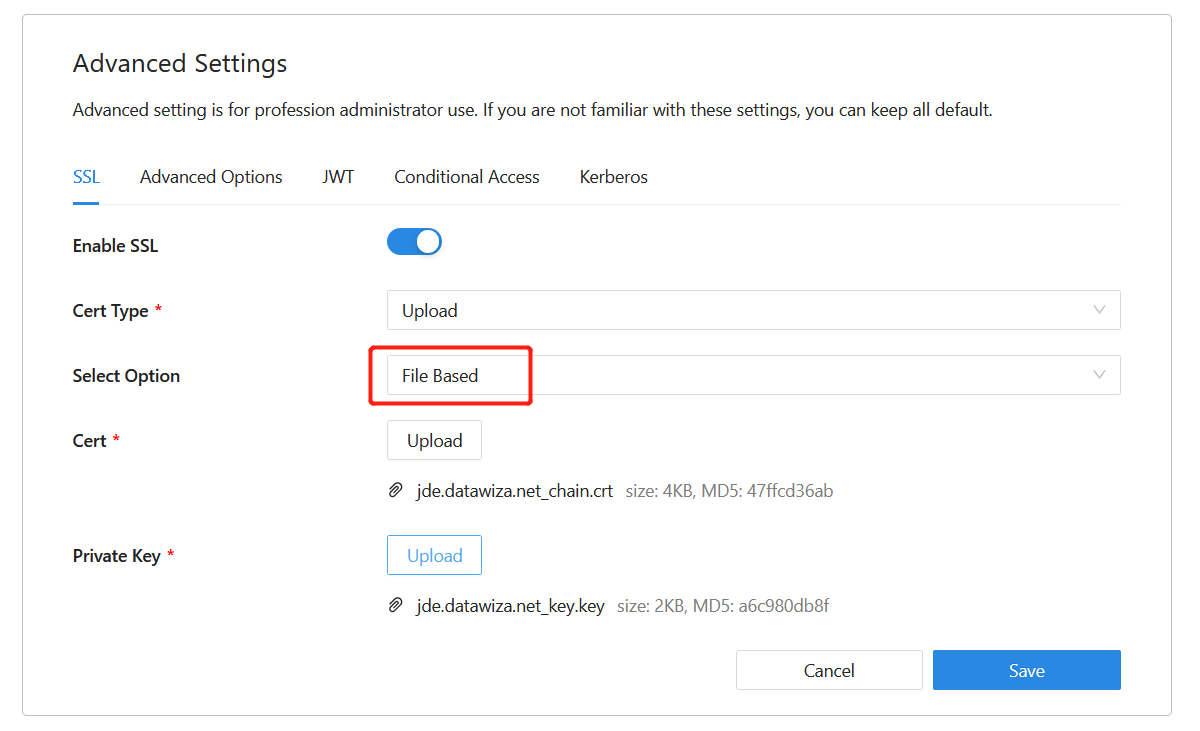
- Click Save.
Enable Single Sign-On in JD Edwards EnterpriseOne console
To enable single sign-on in the JD Edwards environment:
Sign in to the JD Edwards EnterpriseOne Server Manager Management console as an administrator.
In Select Instance , select EnterpriseOne HTML Server.
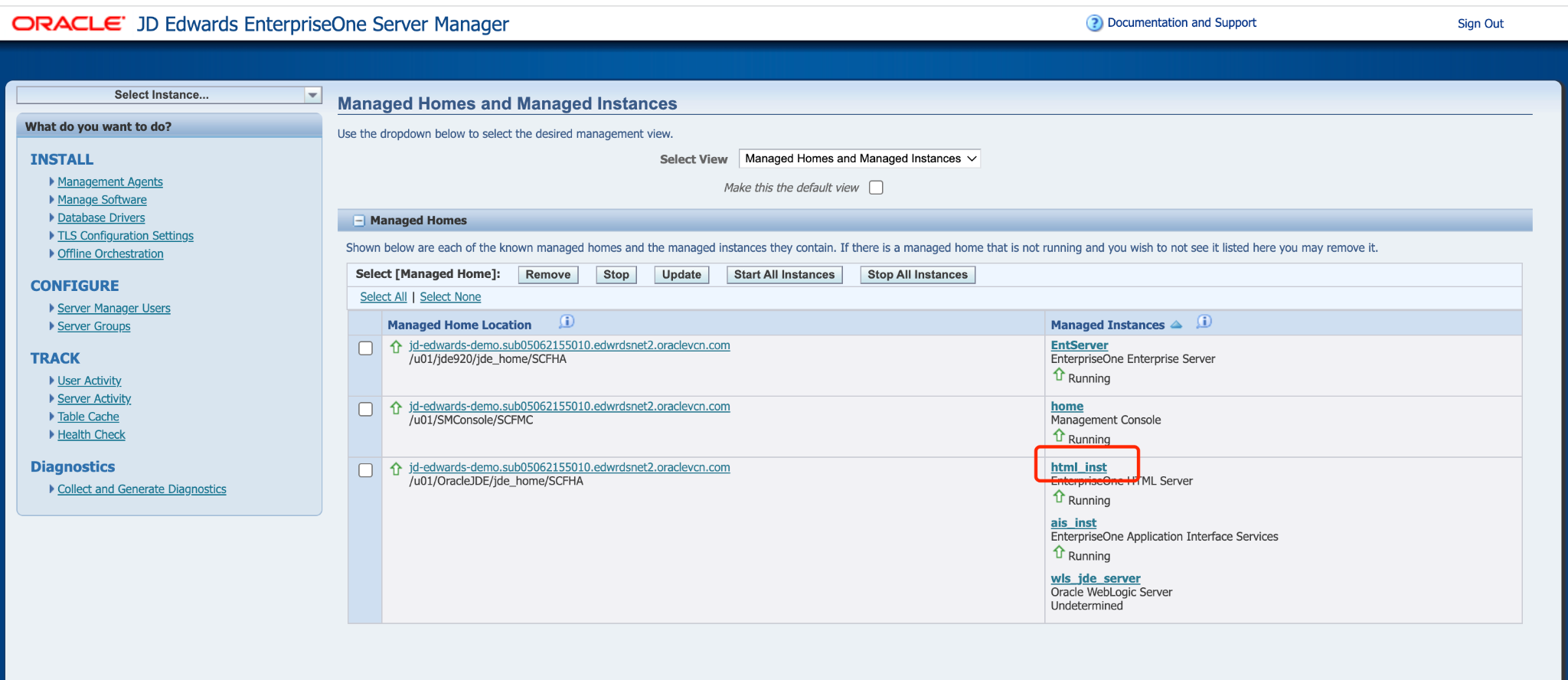
In the Configuration tile, select View as Advanced, and then click Security.
Select the Enable Oracle Access Manager check box, and then enter
/datawiza/ab-logoutin the Oracle Access Manager Sign-Off URL field. In the Security Server Configuration section, click Apply.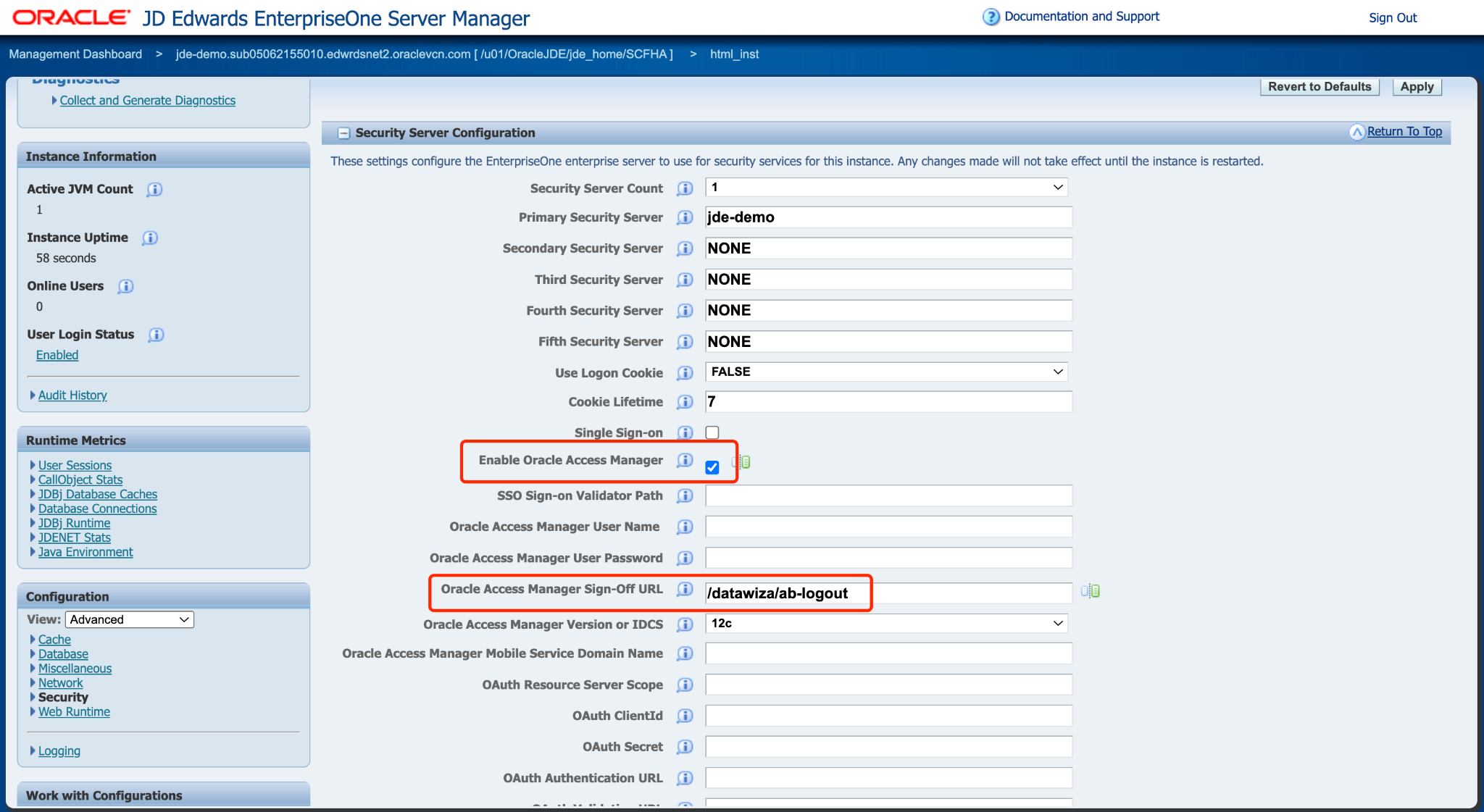
Click Stop and confirm that you want to stop the managed instance. If a message indicates that the web server configuration (jas.ini) is out-of-date, click Synchronize Configuration.
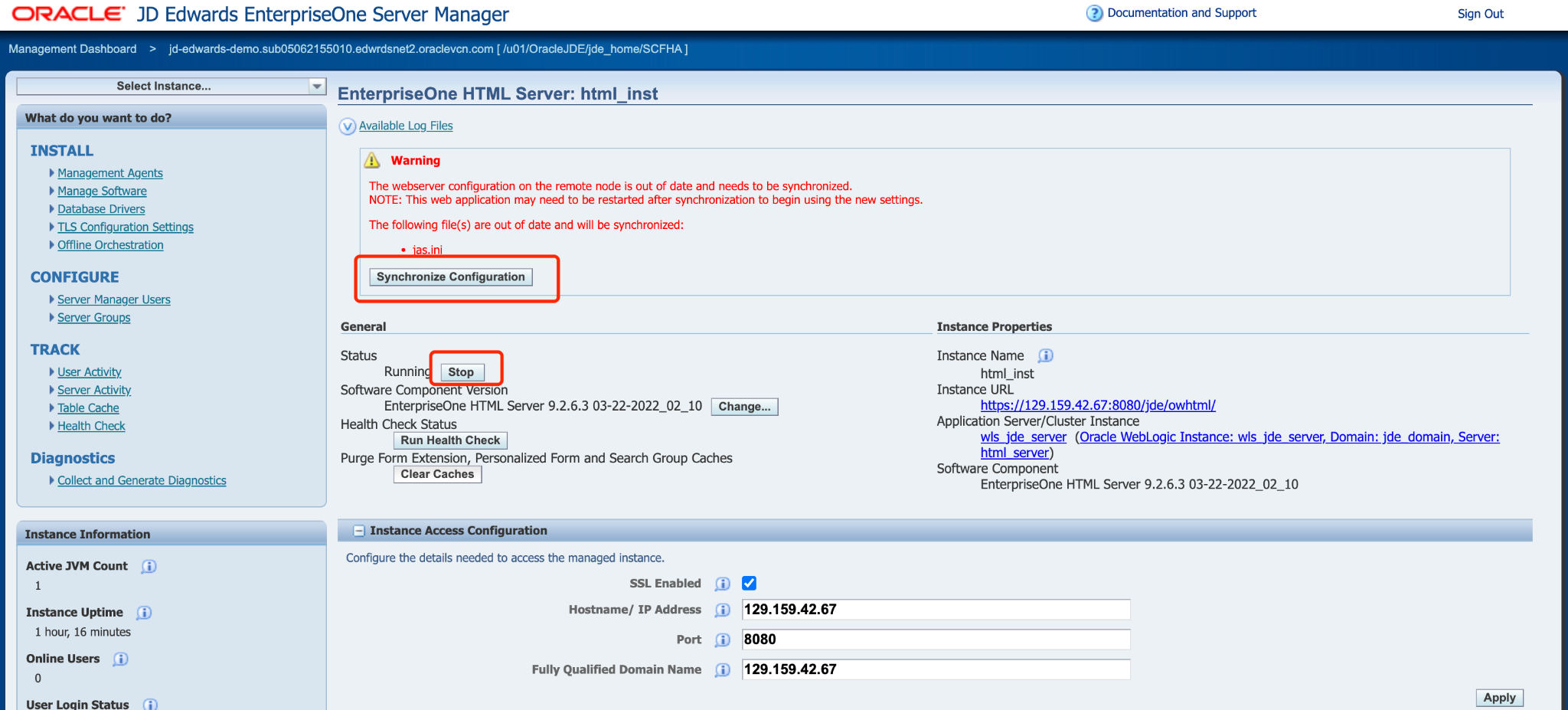
Click Start and confirm that you want to start the managed instance.
(Optional) Enable MFA on Microsoft Entra ID (Formerly Azure AD)
To provide an extra level of security for sign-ins, sometimes you might want to enforce MFA for user sign-in. There are several ways to achieve this. The simplest and easiest way is to enable MFA on the Azure portal.
- Sign in to the Azure portal as a Global Administrator.
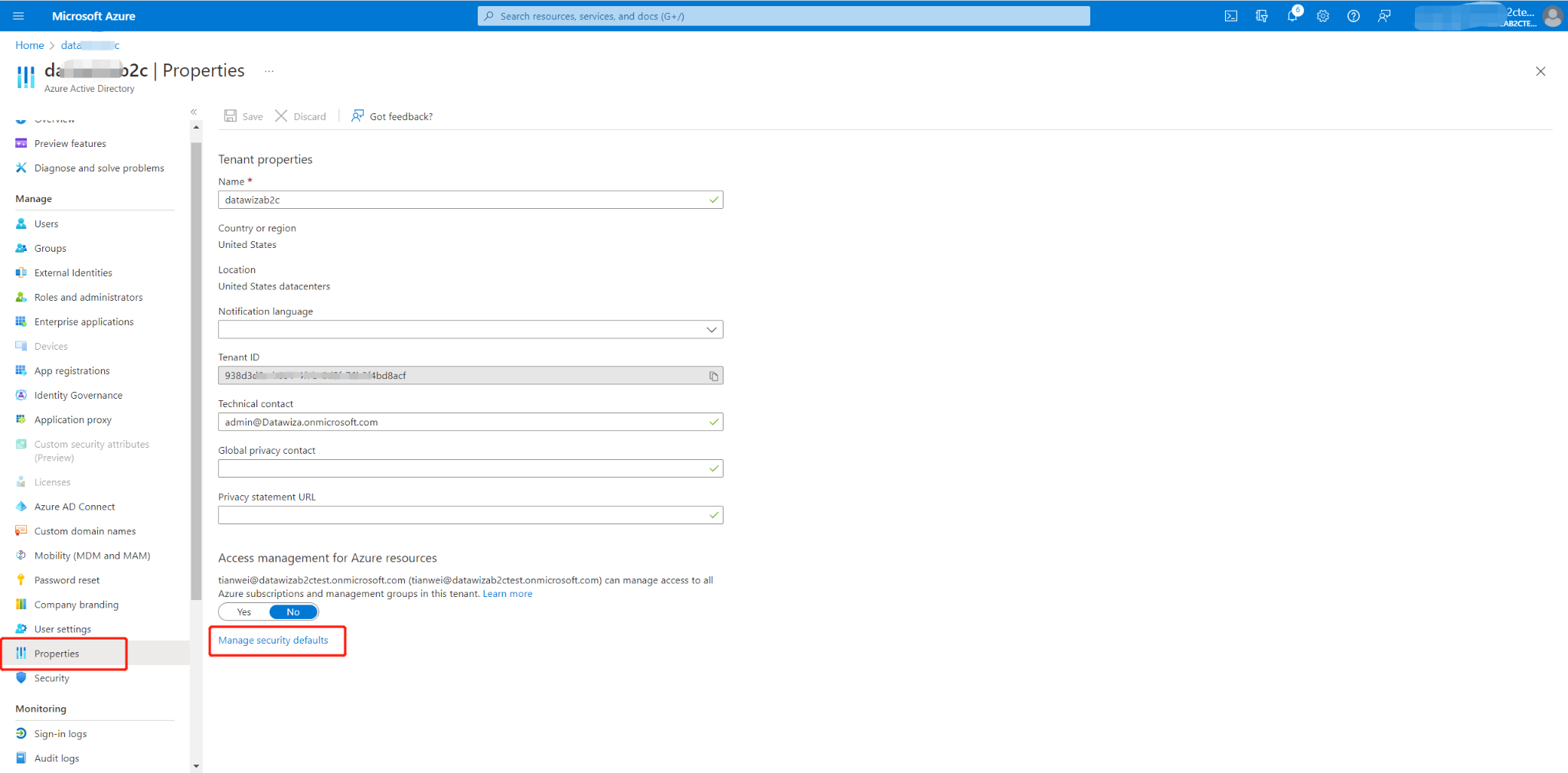
- Select Microsoft Entra ID > Manage > Properties.
- Under Properties , click the Manage security defaults.
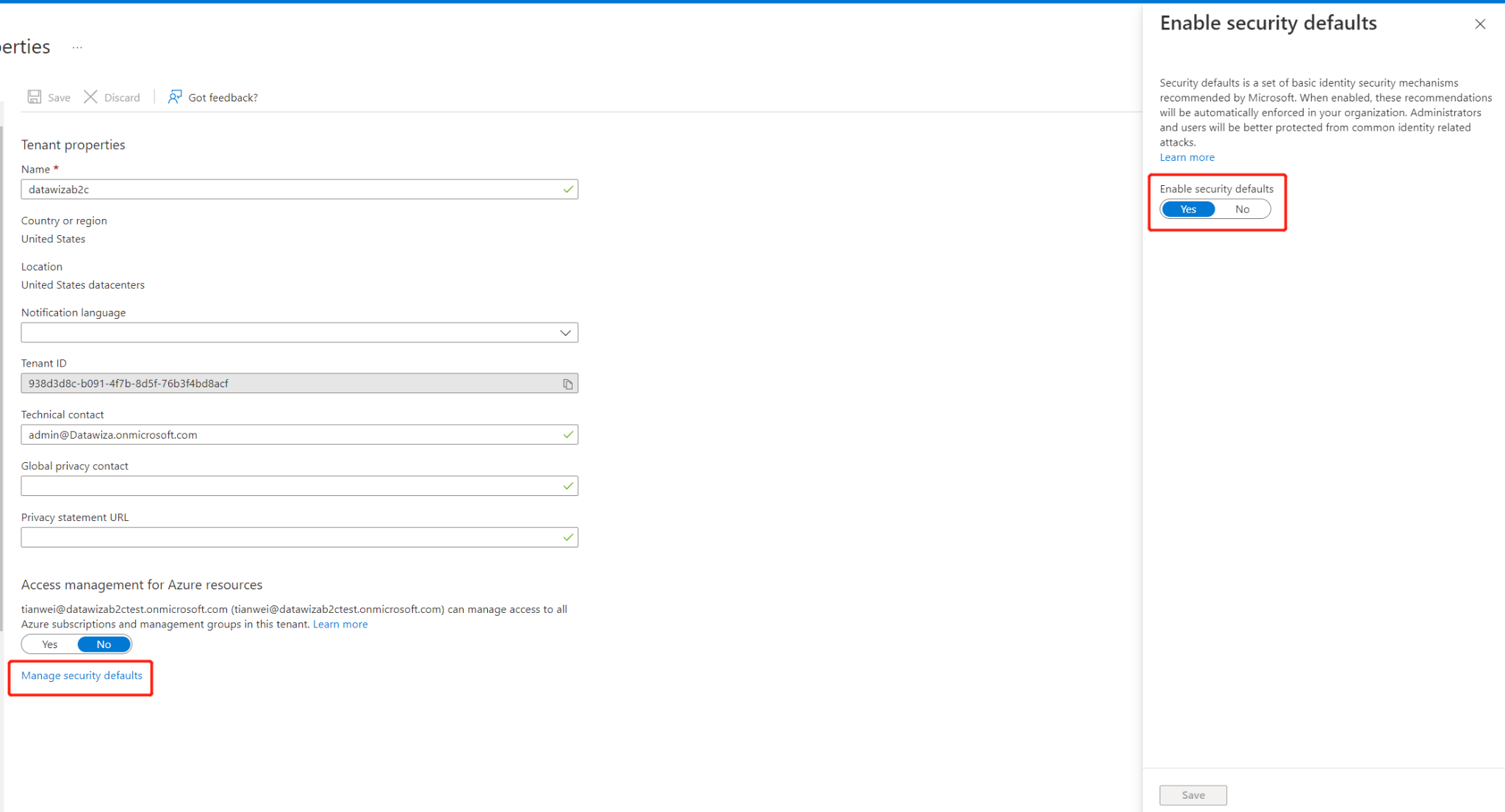
- Under Enable Security defaults, select Yes and then Save.
Test an Oracle JDE application
To confirm SSO and MFA for Oracle JDE application work correctly, a prompt should appear to use an Identity Provider account for signing in. Credentials and optional MFA are checked and the Oracle JDE home page appears.
Note
For security purpose, organizations using this model in production environment should block all direct access to the application, thus forcing the use of a strict path through the Datawiza Access Proxy.
That's it! Here is a video clipshowing the user experience after a successful integration between Microsoft Entra ID and Oracle JDE via Datawiza.
Summary
In this article, you learned how to:
- Configure and Deploy the Datawiza Access Proxy
- Integrate the Datawiza Access Proxy with Oracle JDE
- Enable Microsoft Entra ID SSO login and MFA for Oracle JDE
If you have any questions, don't be afraid to contact us through support email (support@datawiza.com)!
