Datawiza Access Proxy Network Restriction
In this section, we will talk about how to restrict access to the customer's applications. For header-based authentication, we need to make sure that the application is only accessible to the proxy since the application trusts the request header sent by proxy. Depending on how the app is deployed, we can achieve this in different ways:
On the Different Servers
In Cloud
If you use some cloud providers, like AWS, to host your application. You can use functions like Security Group in AWS to control traffic. 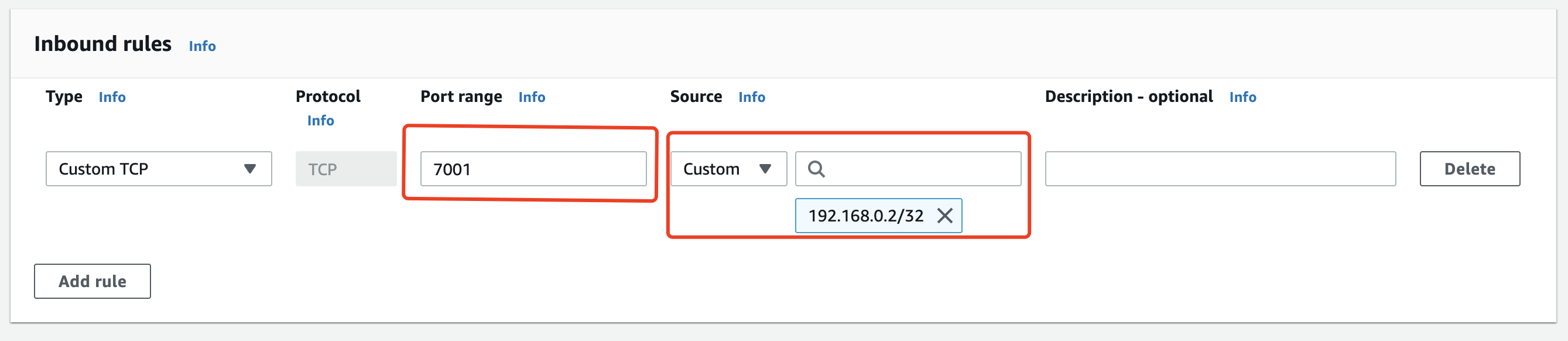 Where 192.168.0.2 is the DAP server address and 7001 is the customer's application running port.
Where 192.168.0.2 is the DAP server address and 7001 is the customer's application running port.
Similarly, you can use Network Security Groups if you are using Azure. 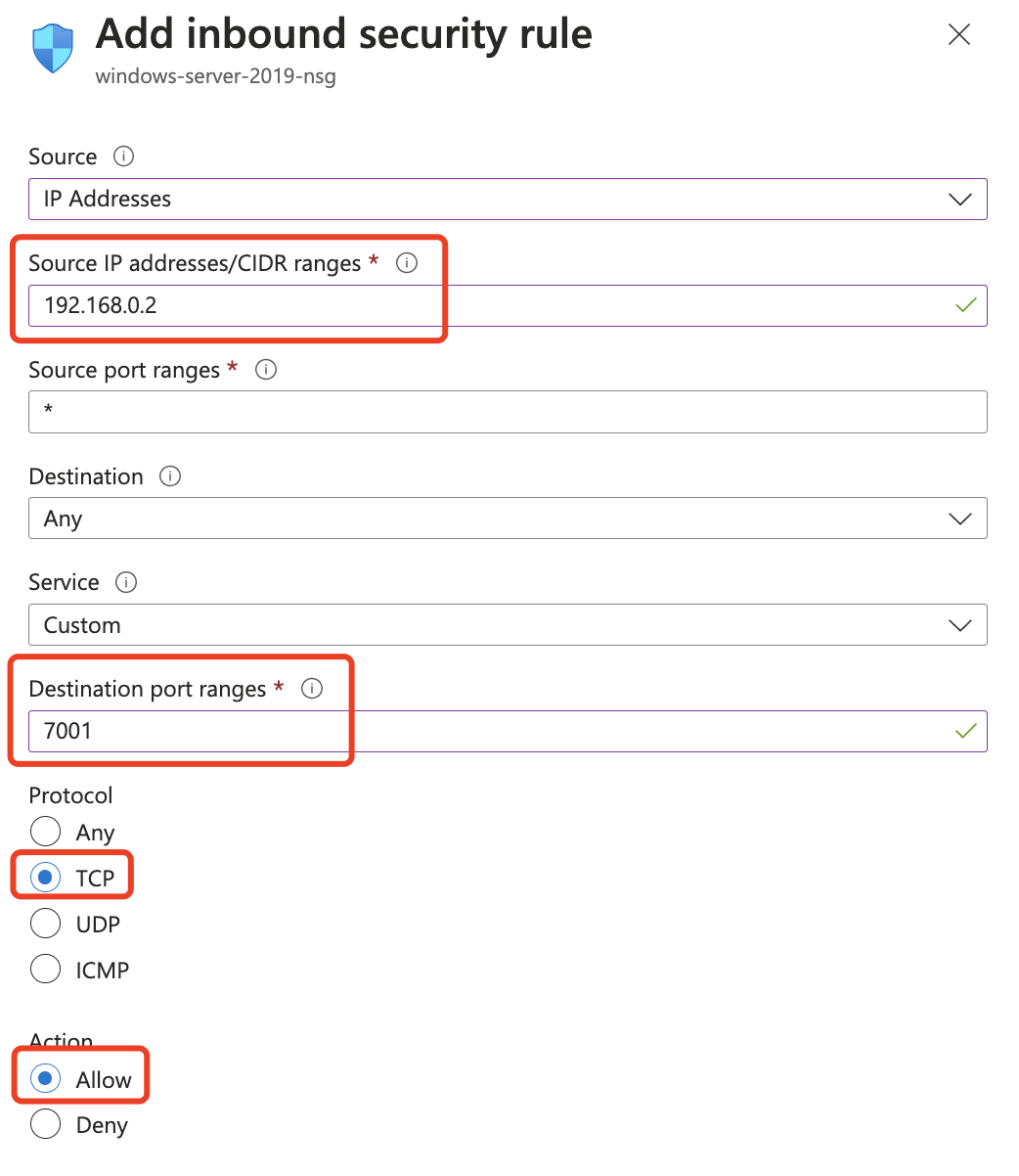 Where 192.168.0.2 is the DAP server address and 7001 is the customer's application running port.
Where 192.168.0.2 is the DAP server address and 7001 is the customer's application running port.
On-Premise
If you deploy DAP and your application on-premise. You can use iptables to restrict access. For example, we assume that your application running on server 192.168.0.1 on port 7001, while DAP running on 192.168.0.2. You can do the following config in the application host (192.168.0.1):
iptables -A INPUT -p tcp --dport 7001 -s 192.168.0.2 -j ACCEPT
iptables -A INPUT -p tcp --dport 7001 -j DROP
This code will allow incoming connections on TCP port 7001 from the Datawiza server IP and block all other incoming connections on the same port.
On the Same Server
Also, you can deploy the DAP along with your applications on the same server. With this deployment mode, you need to open the DAP running port to your users.
In Cloud
Similar to the previous situation, use the DAP running port instead of the customer's application running port, and use the user's IP range instead of the DAP server address:
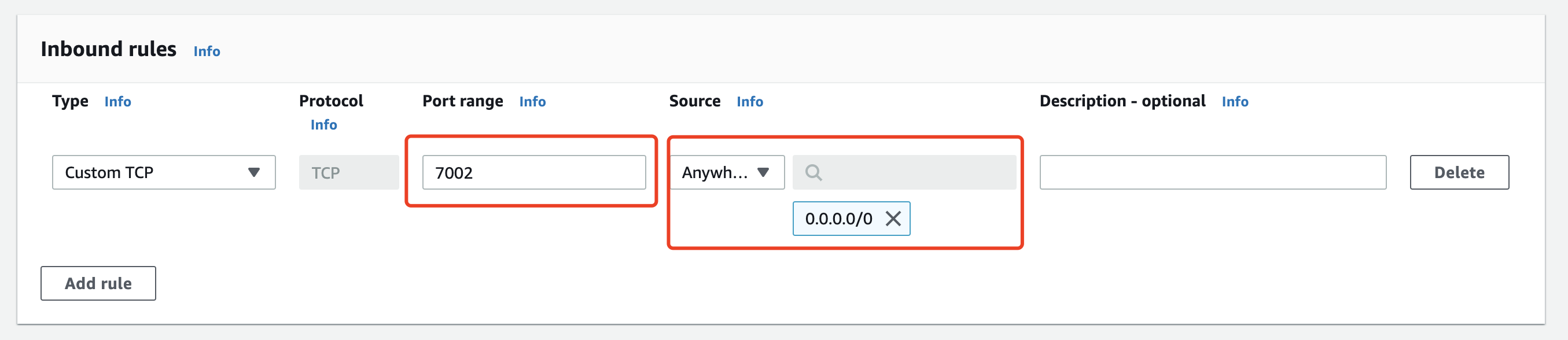
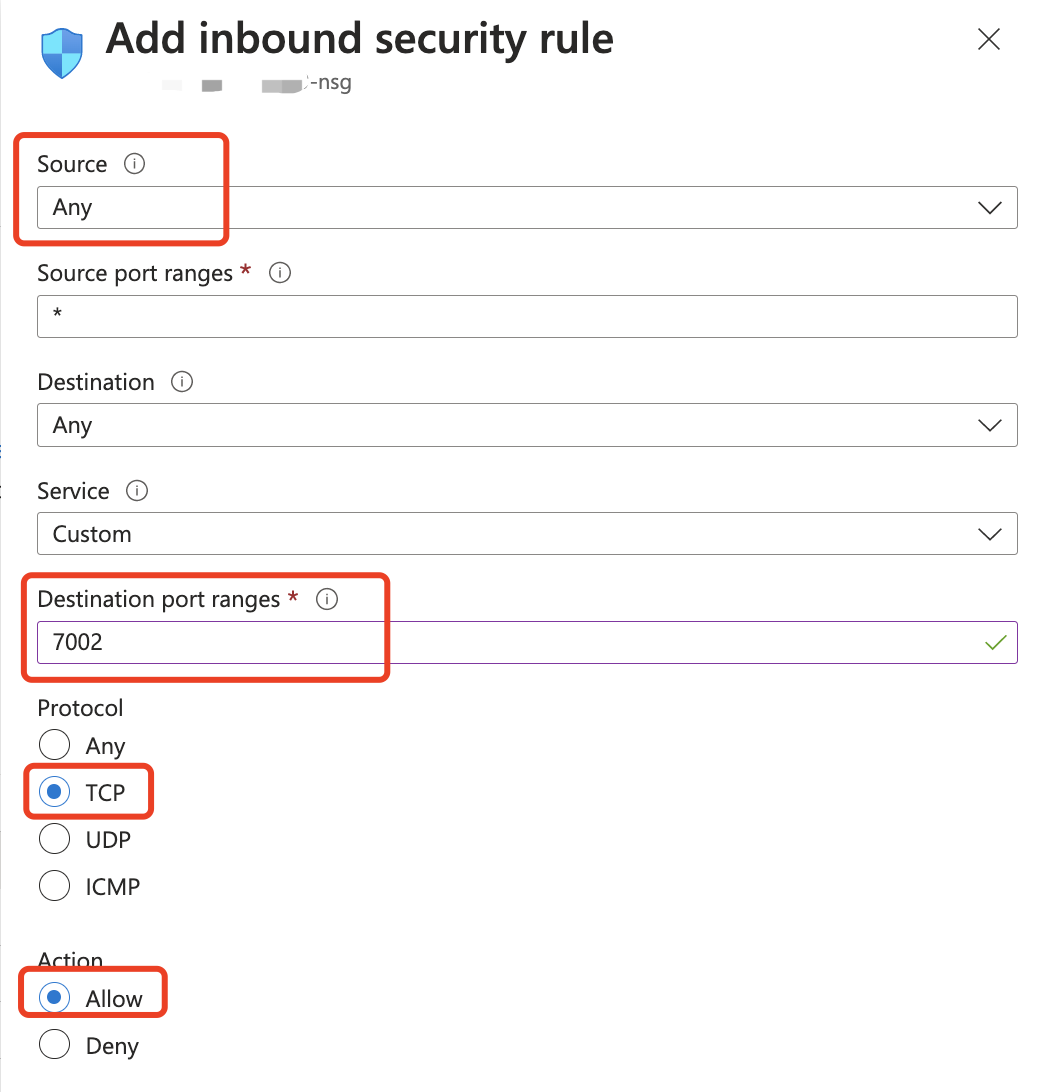
Update the Source accordingly if you don't want to expose the DAP to the public.
On-Premise
Use iptables to restrict access to the DAP running port and drop any other access:
iptables -A INPUT -p tcp --dport 7002 -s <USER IP Range> -j ACCEPT
iptables -A INPUT -p tcp --dport 7002 -j DROP
